By its nature FTP protocol was designed as an insecure protocol and all data and passwords are transferred in plain text, making the job of a third party very easy to intercept all FTP client-server transactions, especially usernames and passwords used in authentication process.

Requirements
- Installing ProFTPD Server on RHEL/CentOS 7
- Enable Anonymous Account for Proftpd Server in RHEL/CentOS 7
This tutorial will guide you on how you can secure and encrypt FTP communication on ProFTPd Server in CentOS/RHEL 7, using TLS (Transport Layer Security) with Explicit FTPS extension (think at FTPS as what HTTPS is for HTTP Protocol).
Step 1: Create Proftpd TLS Module Configuration File
1. As discussed in previous Proftpd tutorial concerning Anonymous account, this guide will also use the same approach on managing Proftpd future configurations files as modules, with the help of enabled_mod and disabled_mod directories, which will host all server’s extended capabilities.
So, create a new file with your favourite text editor named tls.conf in disabled_mod Proftpd path and add the following directives.
# nano /etc/proftpd/disabled_mod/tls.conf
Add following TLS file configuration excerpt.
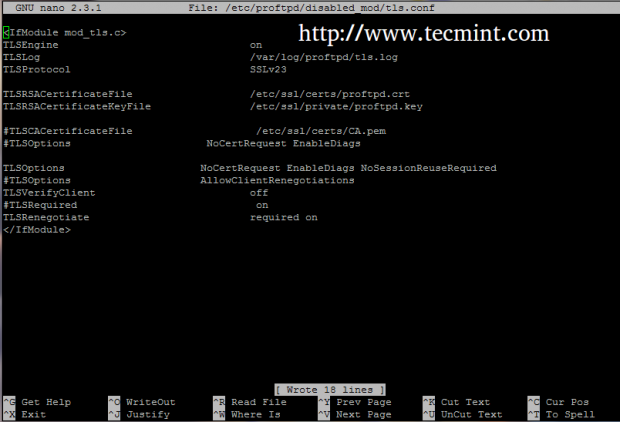
<IfModule mod_tls.c> TLSEngine on TLSLog /var/log/proftpd/tls.log TLSProtocol SSLv23 TLSRSACertificateFile /etc/ssl/certs/proftpd.crt TLSRSACertificateKeyFile /etc/ssl/private/proftpd.key #TLSCACertificateFile /etc/ssl/certs/CA.pem TLSOptions NoCertRequest EnableDiags NoSessionReuseRequired TLSVerifyClient off TLSRequired on TLSRenegotiate required on </IfModule>
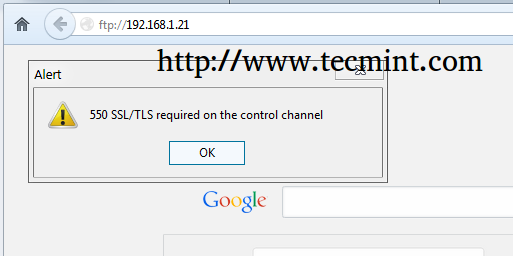
2. If you use browsers or FTP Clients that doesn’t support TLS connections, comment the line TLSRequired on in order to allow TLS and non-TLS connections the same time and avoid the error message as in the screenshot below.
Step 2: Create SSL Certificate Files for TLS
3. After you have created the TLS module configuration file. that will enable FTP over TLS on Proftpd, you need to generate SSL Certificate and Key in order to use secure communication over ProFTPD Server with the help of OpenSSL package.
# yum install openssl
You can use a single long command to generate SSL Certificate and Key pairs, but to simplify things you can create a simple bash script that will generate SSL pairs with your desired name and assign the correct permissions for Key file.
Create a bash file named proftpd_gen_ssl on /usr/local/bin/ or on any other executable system path (defined by $PATH variable).
# nano /usr/local/bin/proftpd_gen_ssl
Add the following content to it.
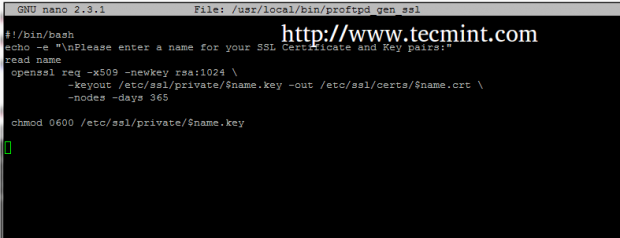
#!/bin/bash
echo -e "\nPlease enter a name for your SSL Certificate and Key pairs:"
read name
openssl req -x509 -newkey rsa:1024 \
-keyout /etc/ssl/private/$name.key -out /etc/ssl/certs/$name.crt \
-nodes -days 365\
chmod 0600 /etc/ssl/private/$name.key
4. After you have created the above file, assign it with execution permissions, assure that /etc/ssl/private directory exist and run the script to create SSL Certificate and Key pairs.
# chmod +x /usr/local/bin/proftpd_gen_ssl # mkdir -p /etc/ssl/private # proftpd_gen_ssl
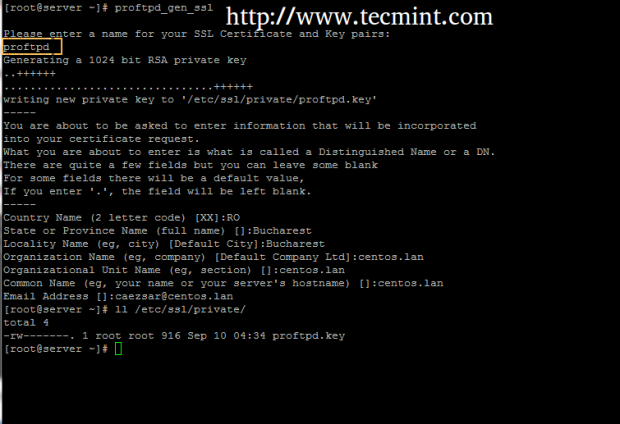
Supply the SSL Certificate with the required prompted information which is self-explanatory, but pay attention to Common Name to match your host Fully Qualified Domain Name – FQDN.
Step 3: Enable TLS on ProFTPD Server
5. As the TLS Configuration file created earlier already points to the right SSL Certificate and Key file the only thing remaining is to activate TLS module by creating a symbolic link of tls.conf file to enabled-mod directory and restart ProFTPD daemon to apply changes.
# ln -s /etc/proftpd/disabled_mod/tls.conf /etc/proftpd/enabled_mod/ # systemctl restart proftpd
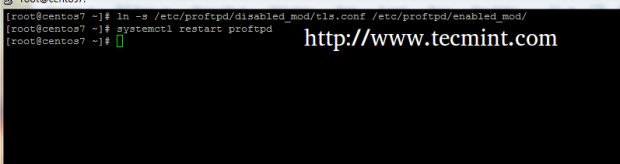
6. To disable TLS module just remove tls.conf symlink from enabled_mod directory and restart ProFTPD server to apply changes.
# rm /etc/proftpd/enabled_mod/tls.conf # systemctl restart proftpd
Step 4: Open Firewall to allow FTP over TLS Communication
7. In order for clients to access ProFTPD and secure transfer files in Passive Mode you must open the entire port range between 1024 and 65534 on RHEL/CentOS Firewall, using the following commands.
# firewall-cmd --add-port=1024-65534/tcp # firewall-cmd --add-port=1024-65534/tcp --permanent # firewall-cmd --list-ports # firewall-cmd --list-services # firewall-cmd --reload
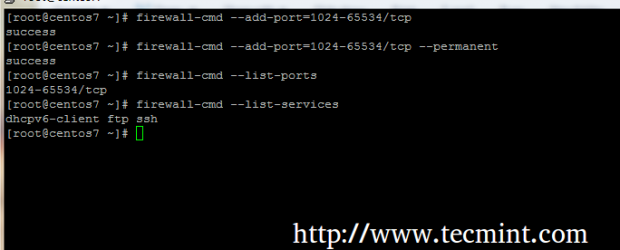
That’s it. Now your system is ready to accept FTP communication over TLS from a Client side.
Step 5: Access ProFTPD over TLS from Clients
8. Web browsers usually have no built-in support for FTP over TLS protocol, so all transaction are delivered over non-encrypted FTP. One of the most excellent FTP Clients is FileZilla, which is entirely Open Source and can run on almost all major Operating Systems.
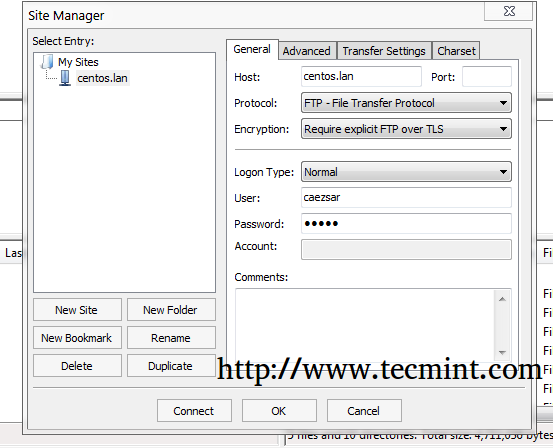
To access FTP over TLS from FileZilla open Site Manager, choose FTP on Protocol and Require explicit FTP over TLS on Encryption drop-down menu, select you Logon Type as Normal, enter your FTP credentials and hit Connect to communicate with the server.
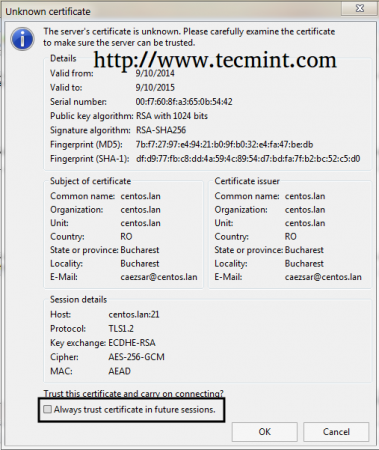
9. If it’s the first time you connect to ProFTPD Server a pop-up with the new Certificate should appear, check the box that says Always trust certificate for future sessions and hit on OK to accept Certificate and authenticate to ProFTPD server.

If you are planning to use other clients than FileZilla to securely access FTP resources make sure that they support FTP over TLS protocol. Some good examples for FTP clients that can speak FTPS are WinSCP for Windows Platforms and gFTP or LFTP (command line) for NIX.





Thank you, sir, you are a lifesaver!
P.S.: This is what I tried:
# openssl req -x509 -newkey rsa:2048 \ -keyout /etc/ssl/private/proftpd.key -out /etc/ssl/certs/proftpd.crt \ -nodes -days 365\ # chmod 0600 /etc/ssl/private/proftpd.key # chmod 0640 /etc/ssl/certs/proftpd.crt # chmod +x /usr/sbin/proftpd-gencert # mkdir -p /etc/ssl/private # cd /etc/ssl/private # proftpd-gencertWhy after install proftpd i not found folder enable_mod and disable_mod and link for tutorial with title enabling anonymous redirect to link install proftpd? is still work? thanks
Use this guidelines but unable to connect outside my home modem. LAN connection is fine. Have any idea what port needed to forward. iptables is disabled and SE linux as well. Please advise.
It works like a charm :)