Guys, if you are a regular reader of tecmint.com you will notice that this is our third article on security tools. In our previous two articles, we have given you all the guidance in how to secure Apache and Linux Systems from Malware, DOS, and DDOS attacks using mod_security and mod_evasive and LMD (Linux Malware Detect).
Again we are here to introduce a new security tool called Rkhunter (Rootkit Hunter). This article will guide you on a way to install and configure RKH (RootKit Hunter) in Linux systems using source code.
What Is Rkhunter?
Rkhunter (Rootkit Hunter) is an open-source Unix/Linux based scanner tool for Linux systems released under GPL that scans backdoors, rootkits, and local exploits on your systems.
It scans hidden files, wrong permissions set on binaries, suspicious strings in the kernel, etc. To know more about Rkhunter and its features visit http://rkhunter.sourceforge.net/.
Install Rootkit Hunter Scanner in Linux Systems
Step 1: Downloading Rkhunter
First, download the latest stable version of the Rkhunter tool by going to http://rkhunter.sourceforge.net/ or use the below Wget command to download it on your systems.
# cd /tmp # wget http://downloads.sourceforge.net/project/rkhunter/rkhunter/1.4.6/rkhunter-1.4.6.tar.gz
Step 2: Installing Rkhunter
Once you have downloaded the latest version, run the following commands as a root user to install it.
# tar -xvf rkhunter-1.4.6.tar.gz # cd rkhunter-1.4.6 # ./installer.sh --layout default --install
Sample Output
Checking system for: Rootkit Hunter installer files: found A web file download command: wget found Starting installation: Checking installation directory "/usr/local": it exists and is writable. Checking installation directories: Directory /usr/local/share/doc/rkhunter-1.4.2: creating: OK Directory /usr/local/share/man/man8: exists and is writable. Directory /etc: exists and is writable. Directory /usr/local/bin: exists and is writable. Directory /usr/local/lib64: exists and is writable. Directory /var/lib: exists and is writable. Directory /usr/local/lib64/rkhunter/scripts: creating: OK Directory /var/lib/rkhunter/db: creating: OK Directory /var/lib/rkhunter/tmp: creating: OK Directory /var/lib/rkhunter/db/i18n: creating: OK Directory /var/lib/rkhunter/db/signatures: creating: OK Installing check_modules.pl: OK Installing filehashsha.pl: OK Installing stat.pl: OK Installing readlink.sh: OK Installing backdoorports.dat: OK Installing mirrors.dat: OK Installing programs_bad.dat: OK Installing suspscan.dat: OK Installing rkhunter.8: OK Installing ACKNOWLEDGMENTS: OK Installing CHANGELOG: OK Installing FAQ: OK Installing LICENSE: OK Installing README: OK Installing language support files: OK Installing ClamAV signatures: OK Installing rkhunter: OK Installing rkhunter.conf: OK Installation complete
Step 3: Updating Rkhunter
Run the RKH updater to fill the database properties by running the following command.
# /usr/local/bin/rkhunter --update # /usr/local/bin/rkhunter --propupd
Sample Output
[ Rootkit Hunter version 1.4.6 ] Checking rkhunter data files... Checking file mirrors.dat [ Updated ] Checking file programs_bad.dat [ No update ] Checking file backdoorports.dat [ No update ] Checking file suspscan.dat [ No update ] Checking file i18n/cn [ No update ] Checking file i18n/de [ No update ] Checking file i18n/en [ No update ] Checking file i18n/tr [ No update ] Checking file i18n/tr.utf8 [ No update ] Checking file i18n/zh [ No update ] Checking file i18n/zh.utf8 [ No update ] Checking file i18n/ja [ No update ] File created: searched for 177 files, found 131, missing hashes 1
Step 4: Setting Cronjob and Email Alerts
Create a file called rkhunter.sh under /etc/cron.daily/, which then scans your file system every day and sends email notifications to your email id. Create the following file with the help of your favorite editor.
# vi /etc/cron.daily/rkhunter.sh
Add the following lines of code to it and replace “YourServerNameHere” with your “Server Name” and “your@email.com” with your “Email Id“.
#!/bin/sh ( /usr/local/bin/rkhunter --versioncheck /usr/local/bin/rkhunter --update /usr/local/bin/rkhunter --cronjob --report-warnings-only ) | /bin/mail -s 'rkhunter Daily Run (PutYourServerNameHere)' your@email.com
Set execute permission on the file.
# chmod 755 /etc/cron.daily/rkhunter.sh
Step 5: Manual Scan and Usage
To scan the entire file system, run the Rkhunter as a root user.
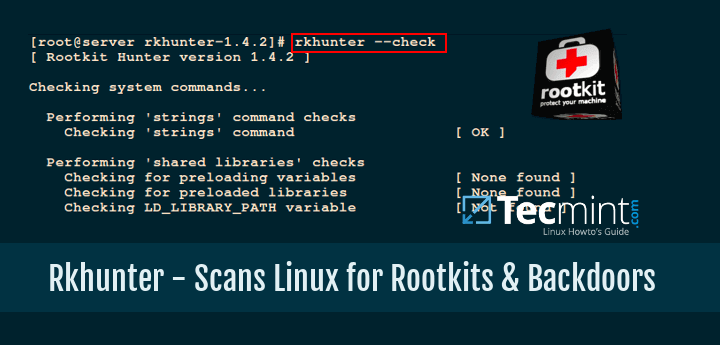
# rkhunter --check
Sample Output
[ Rootkit Hunter version 1.4.6 ]
Checking system commands...
Performing 'strings' command checks
Checking 'strings' command [ OK ]
Performing 'shared libraries' checks
Checking for preloading variables [ None found ]
Checking for preloaded libraries [ None found ]
Checking LD_LIBRARY_PATH variable [ Not found ]
Performing file properties checks
Checking for prerequisites [ OK ]
/usr/local/bin/rkhunter [ OK ]
/usr/sbin/adduser [ OK ]
/usr/sbin/chkconfig [ OK ]
/usr/sbin/chroot [ OK ]
/usr/sbin/depmod [ OK ]
/usr/sbin/fsck [ OK ]
/usr/sbin/fuser [ OK ]
/usr/sbin/groupadd [ OK ]
/usr/sbin/groupdel [ OK ]
/usr/sbin/groupmod [ OK ]
/usr/sbin/grpck [ OK ]
/usr/sbin/ifconfig [ OK ]
/usr/sbin/ifdown [ Warning ]
/usr/sbin/ifup [ Warning ]
/usr/sbin/init [ OK ]
/usr/sbin/insmod [ OK ]
/usr/sbin/ip [ OK ]
/usr/sbin/lsmod [ OK ]
/usr/sbin/lsof [ OK ]
/usr/sbin/modinfo [ OK ]
/usr/sbin/modprobe [ OK ]
/usr/sbin/nologin [ OK ]
/usr/sbin/pwck [ OK ]
/usr/sbin/rmmod [ OK ]
/usr/sbin/route [ OK ]
/usr/sbin/rsyslogd [ OK ]
/usr/sbin/runlevel [ OK ]
/usr/sbin/sestatus [ OK ]
/usr/sbin/sshd [ OK ]
/usr/sbin/sulogin [ OK ]
/usr/sbin/sysctl [ OK ]
/usr/sbin/tcpd [ OK ]
/usr/sbin/useradd [ OK ]
/usr/sbin/userdel [ OK ]
/usr/sbin/usermod [ OK ]
....
[Press to continue]
Checking for rootkits...
Performing check of known rootkit files and directories
55808 Trojan - Variant A [ Not found ]
ADM Worm [ Not found ]
AjaKit Rootkit [ Not found ]
Adore Rootkit [ Not found ]
aPa Kit [ Not found ]
.....
[Press to continue]
Performing additional rootkit checks
Suckit Rookit additional checks [ OK ]
Checking for possible rootkit files and directories [ None found ]
Checking for possible rootkit strings [ None found ]
....
[Press to continue]
Checking the network...
Performing checks on the network ports
Checking for backdoor ports [ None found ]
....
Performing system configuration file checks
Checking for an SSH configuration file [ Found ]
Checking if SSH root access is allowed [ Warning ]
Checking if SSH protocol v1 is allowed [ Warning ]
Checking for a running system logging daemon [ Found ]
Checking for a system logging configuration file [ Found ]
Checking if syslog remote logging is allowed [ Not allowed ]
...
System checks summary
=====================
File properties checks...
Files checked: 137
Suspect files: 6
Rootkit checks...
Rootkits checked : 383
Possible rootkits: 0
Applications checks...
Applications checked: 5
Suspect applications: 2
The system checks took: 5 minutes and 38 seconds
All results have been written to the log file: /var/log/rkhunter.log
One or more warnings have been found while checking the system.
Please check the log file (/var/log/rkhunter.log)
The above command generates a log file under /var/log/rkhunter.log with the check results made by Rkhunter.
# cat /var/log/rkhunter.log
Sample Output
[11:21:04] Running Rootkit Hunter version 1.4.6 on tecmint [11:21:04] [11:21:04] Info: Start date is Mon Dec 21 11:21:04 AM IST 2020 [11:21:04] [11:21:04] Checking configuration file and command-line options... [11:21:04] Info: Detected operating system is 'Linux' [11:21:04] Info: Found O/S name: Fedora release 33 (Thirty Three) [11:21:04] Info: Command line is /usr/local/bin/rkhunter --check [11:21:04] Info: Environment shell is /bin/bash; rkhunter is using bash [11:21:04] Info: Using configuration file '/etc/rkhunter.conf' [11:21:04] Info: Installation directory is '/usr/local' [11:21:04] Info: Using language 'en' [11:21:04] Info: Using '/var/lib/rkhunter/db' as the database directory [11:21:04] Info: Using '/usr/local/lib64/rkhunter/scripts' as the support script directory [11:21:04] Info: Using '/usr/local/sbin /usr/local/bin /usr/sbin /usr/bin /bin /sbin /usr/libexec /usr/local/libexec' as the command directories [11:21:04] Info: Using '/var/lib/rkhunter/tmp' as the temporary directory [11:21:04] Info: No mail-on-warning address configured [11:21:04] Info: X will be automatically detected [11:21:04] Info: Found the 'basename' command: /usr/bin/basename [11:21:04] Info: Found the 'diff' command: /usr/bin/diff [11:21:04] Info: Found the 'dirname' command: /usr/bin/dirname [11:21:04] Info: Found the 'file' command: /usr/bin/file [11:21:04] Info: Found the 'find' command: /usr/bin/find [11:21:04] Info: Found the 'ifconfig' command: /usr/sbin/ifconfig [11:21:04] Info: Found the 'ip' command: /usr/sbin/ip [11:21:04] Info: Found the 'ipcs' command: /usr/bin/ipcs [11:21:04] Info: Found the 'ldd' command: /usr/bin/ldd [11:21:04] Info: Found the 'lsattr' command: /usr/bin/lsattr ...
For more information and options please run the following command.
# rkhunter --help
If you liked this article, then sharing is the right way to say thanks.




Does it explain what to do when something is detected? Also, what does a warning mean? I got it on one file, and in your example, you showed two warnings – what does this mean?
Thanks for the article and the clear instructions too.
try the sudo bash command to get root access, and then it will allow.
What’s the server name?
This whole rkhunter probably only scans the most important changes in the system, but when it comes to removing viruses – it doesn’t. Does anyone know of console antivirus that automatically deals with threats?
@Programoanie,
Check this article: The 8 Best Free Anti-Virus Programs for Linux
Debcheckroot – That also detects a rootkit which is not known by any database (like f.i. NSA rootkits).
It verifies the sha256 sums of files in the Debian/Ubuntu packages.
The most useful comment on here by a million, cheers!
$ sudo apt-get install forensics-all mac-robber unhide unhide.rb
I am looking for alternate of rkhunter
$ [sudo] apt-get install chkrootkit
I tried unpacking and installing rkhunter from /tmp as indicated in the instructions above but got the error “-bash: ./installer.sh: Permission denied“. So I tried chmod u+x installer.sh.
Still didn’t work. After a bit of searching, I found out that on my system the /tmp directory is mounted without execution permissions. I moved the rkhunter installation directory to ~ and successfully ran the rkhunter installer from that location. Thanks.
Just use the repositories… (any will do)
https://www.elstel.org/debcheckroot/ (website looks legit and email OK)
Did you check this one? I have problems with importing the key. I also have to cut down on screen time.
To install rkhunter on my Fedora, I don’t have to dowload rkhunter installer but I executed the following command : $ sudo dnf install rkhunter-1.4.2-11.fc24.noarch .
@Khairul,
Thanks for sharing the tip, that means rkhunter included in the recent version of Fedora repositories, that’s good to know, at least we can keep it updated via dnf package manager..
I have a specific requirement. I want to configure rkit runner but my requirement is to check remote windows machine within the same network to be checked via rkit runner that is installed in a Linux box under the same network.Is it feasible to attain?
Thanks for all that you do Ravi, so I followed your instructions and when I got to the last run of step 2 I get a permission denied instead of the sample output you indicated. What might be wrong?
@Kevin,
Thanks for appreciating my work, regarding your problem, you should be root or sudo users to execute those commands shown in Step 2.
Thanks, yes I am logged in as root and have also tried sudo but it failed. I went ahead and purchased the paid version from Admin Ahead and there we discovered a major issue with the server. Need to fix that in order to proceed, thanks again for all your help.
Hi,
Is it possible to monitor changes of a custom file in rkhunter ?
Suppose if I want to monitor if “/etc/hosts file” has changed. How do i track that ?
@Jerald,
I think it’s possible, you can find the option for tracking single file in manual page of Rkhunter or run:
very help full and easy to follow instructions. clean and clear to say. Thanks a lot Mr. Ravi ji.
Hi,
Thanks for your nice job, even a newcomer on Linux like me found it easy to follow.
Keep on this excellent track.
Best Regards,
Sacha
@Sacha,
Thanks for liking our article, yes we always make sure that each article is simple to follow for newbies..
Hi,
Thanks a lot for very useful and nice article
When I run /usr/local/bin/rkhunter –cronjob –report-warnings-only I get a bunch of warnings about executables being replaced by perl scripts. What is that? It makes me nervous because I have to run rkhunter as root. What is it doing? Are these false positives? This is the warning: Warning: The command ‘/usr/sbin/adduser’ has been replaced by a script: /usr/sbin/adduser: Perl script, ASCII text executable
I found this, which makes me feel a little better about the warnings: https://serverfault.com/questions/229942/warning-flagged-by-the-rkhunter
@Andy,
Yes, no need to worry about much these warning, as this updates the database of files that rkhunter knows.
Can i use it to see rootkit on other machines??
@Ruben,
Unfortunately, no you can’t it must be installed on the Linux machine to see rootkits…
is that the right link? I went to the linked website and didn’t see rkhunter. I saw “lynis” which looked similar.
@Paul,
Sorry for trouble, actually the project is moved here: https://www.rootkit.nl/projects/rootkit_hunter.html
I don’t know for how long this software will continue to be updated, in the website it is listed as “older products”. Another minus evaluation is that this is a software created and maintained by one person.
@Martin,
We will keep update this article, until the author stops development, yes it’s older, but its still works better..
Thanks, easy to follow for a novice. I only have one problem in that I get emails daily but they have no content, ie blank. how do I get some kind of report (content). Thanks
@Hany,
Did you see any scan messages in /var/log/rkhunter.log file, this file generated by Rkhunter with check results. Could you share the logs with us?
Forgot to mention that I am installing on a clean server re-image and this is the 1st product I installed.
@Hany,
That’s really good to hear, welcome to Linux world of things. Regarding reports, you should wait for some days to get the full scan report of your Linux server, just have patience and good luck for your Linux future..
Thanks for a useful and concise article. This saved me a bunch of time and helped me feel secure in my recent server setup. One thing though – I’m on CentOS 7 with the epel repo enabled and I was able to install rkhunter with yum which also created a more complex daily cron for me. For email alerts all I had to do was change two config files (/etc/sysconfig/rkhunter for daily output and /etc/rkhunter.conf for just warning alerts)
The epel repo seems popular enough that this method might be better for anyone who already has it enabled, or at least a mention that it’s an option.
whether rkhunter deleting suspected file or give alert only ?
Good tool, but one question though – Most of my systems do not have direct access to internet. So I usually use a jump server where I setup my software repositories, etc
Any suggestions to how I could run /usr/local/bin/rkhunter –update on satellite server and run updates off of that server?
Great! thank you
Thanks for sharing!
Update – New Links and Commands:
# cd /tmp
# wget http://cznic.dl.sourceforge.net/project/rkhunter/rkhunter/1.4.2/rkhunter-1.4.2.tar.gz
# tar -xvf rkhunter-1.4.2.tar.gz
# cd rkhunter-1.4.2
# sh ./installer.sh –layout default –install
…..
all else is the same as above
Michale, thanks for the instructions will update it by today..
@Michael,
Sorry for such a delay in updating this article with new instructions as you suggested, now the article is updated with version 1.4.2..
Hello, when I try to add the code to email me send reports automatically.
I get this bug.
Thank you.
E486: Pattern not found: bin
Thanks a lot.
Figured it out. Installed in a different directory than /tmp and it worked: /opt
I get: ./installer.sh –layout default –install
-bash: ./installer.sh: Permission denied
any ideas?
thank u nice tutorial
Thanks :)
Try “rkhunter –check” instead of “rkhunter –check”
I have this installed but when I run rkhunter –check command not found.
is there any alternate of rootkit Hunter for window?? because Rootkit is Linux base and i want this type of software for window.please help me,i will be very thankful to you for your help.
Thanks !!!
Thanks for this good tutorial. Installation is easy and warning error are listed in the log files to check later, very nice, thanks
Thanks, it’s greate that rkhunter install on our box, can you give some advice for av in centos box or whm/cpanel besides clamav?