A LFCE (Linux Foundation Certified Engineer) is a professional who has the necessary skills to install, manage, and troubleshoot network services in Linux systems, and is in charge of the design, implementation and ongoing maintenance of the system architecture in its entirety.

Introducing The Linux Foundation Certification Program.
In previous posts we discussed how to install Squid + squidGuard and how to configure squid to properly handle or restrict access requests. Please make sure you go over those two tutorials and install both Squid and squidGuard before proceeding as they set the background and the context for what we will cover in this post: integrating squidguard in a working squid environment to implement blacklist rules and content control over the proxy server.
Requirements
- Install Squid and SquidGuard – Part 1
- Configuring Squid Proxy Server with Restricted Access – Part 5
What Can / Cannot I use SquidGuard For?
Though squidGuard will certainly boost and enhance Squid’s features, it is important to highlight what it can and what it cannot do.
squidGuard can be used to:
- limit the allowed web access for some users to a list of accepted/well known web servers and/or URLs only, while denying access to other blacklisted web servers and/or URLs.
- block access to sites (by IP address or domain name) matching a list of regular expressions or words for some users.
- require the use of domain names/prohibit the use of IP address in URLs.
- redirect blocked URLs to error or info pages.
- use distinct access rules based on time of day, day of the week, date etc.
- implement different rules for distinct user groups.
However, neither squidGuard nor Squid can be used to:
- analyze text inside documents and act in result.
- detect or block embedded scripting languages like JavaScript, Python, or VBscript inside HTML code.
BlackLists – The Basics
Blacklists are an essential part of squidGuard. Basically, they are plain text files that will allow you to implement content filters based on specific keywords. There are both freely available and commercial blacklists, and you can find the download links in the squidguard blacklists project’s website.
In this tutorial I will show you how to integrate the blacklists provided by Shalla Secure Services to your squidGuard installation. These blacklists are free for personal / non-commercial use and are updated on a daily basis. They include, as of today, over 1,700,000 entries.
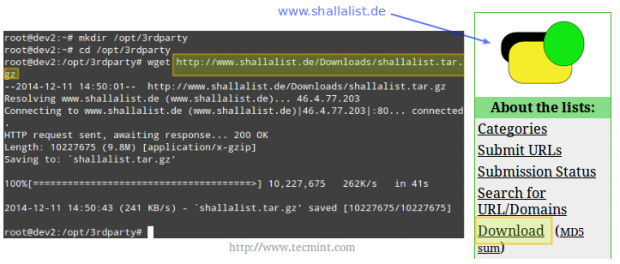
For our convenience, let’s create a directory to download the blacklist package.
# mkdir /opt/3rdparty # cd /opt/3rdparty # wget http://www.shallalist.de/Downloads/shallalist.tar.gz
The latest download link is always available as highlighted below.
After untarring the newly downloaded file, we will browse to the blacklist (BL) folder.
# tar xzf shallalist.tar.gz # cd BL # ls
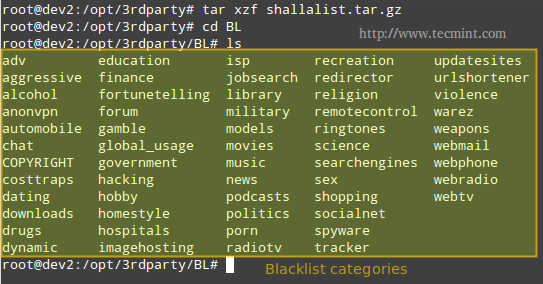
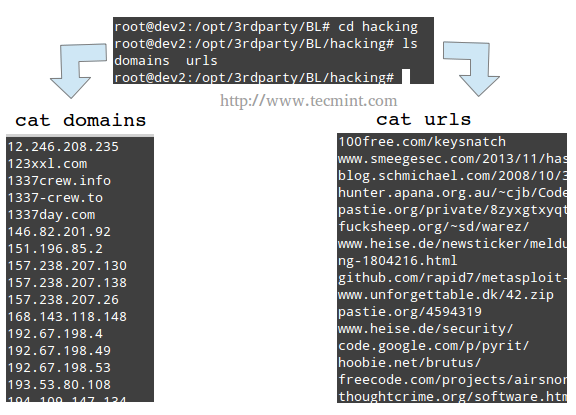
You can think of the directories shown in the output of ls as backlist categories, and their corresponding (optional) subdirectories as subcategories, descending all the way down to specific URLs and domains, which are listed in the files urls and domains, respectively. Refer to the below image for further details.
Installing Blacklists
Installation of the whole blacklist package, or of individual categories, is performed by copying the BL directory, or one of its subdirectories, respectively, to the /var/lib/squidguard/db directory.
Of course you could have downloaded the blacklist tarball to this directory in the first place, but the approach explained earlier gives you more control over what categories should be blocked (or not) at a specific time.
Next, I will show you how to install the anonvpn, hacking, and chat blacklists and how to configure squidGuard to use them.
Step 1: Copy recursively the anonvpn, hacking, and chat directories from /opt/3rdparty/BL to /var/lib/squidguard/db.
# cp -a /opt/3rdparty/BL/anonvpn /var/lib/squidguard/db # cp -a /opt/3rdparty/BL/hacking /var/lib/squidguard/db # cp -a /opt/3rdparty/BL/chat /var/lib/squidguard/db
Step 2: Use the domains and urls files to create squidguard’s database files. Please note that the following command will work for creating .db files for all the installed blacklists – even when a certain category has 2 or more subcategories.
# squidGuard -C all
Step 3: Change the ownership of the /var/lib/squidguard/db/ directory and its contents to the proxy user so that Squid can read the database files.
# chown -R proxy:proxy /var/lib/squidguard/db/
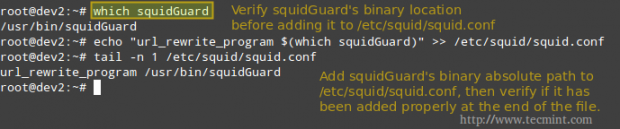
Step 4: Configure Squid to use squidGuard. We will use Squid’s url_rewrite_program directive in /etc/squid/squid.conf to tell Squid to use squidGuard as a URL rewriter / redirector.
Add the following line to squid.conf, making sure that /usr/bin/squidGuard is the right absolute path in your case.
# which squidGuard # echo "url_rewrite_program $(which squidGuard)" >> /etc/squid/squid.conf # tail -n 1 /etc/squid/squid.conf
Step 5: Add the necessary directives to squidGuard’s configuration file (located in /etc/squidguard/squidGuard.conf).
Please refer to the screenshot above, after the following code for further clarification.
src localnet {
ip 192.168.0.0/24
}
dest anonvpn {
domainlist anonvpn/domains
urllist anonvpn/urls
}
dest hacking {
domainlist hacking/domains
urllist hacking/urls
}
dest chat {
domainlist chat/domains
urllist chat/urls
}
acl {
localnet {
pass !anonvpn !hacking !chat !in-addr all
redirect http://www.lds.org
}
default {
pass local none
}
}
Step 6: Restart Squid and test.
# service squid restart [sysvinit / Upstart-based systems] # systemctl restart squid.service [systemctl-based systems]
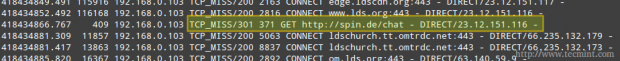
Open a web browser in a client within local network and browse to a site found in any of the blacklist files (domains or urls – we will use http://spin.de/ chat in the following example) and you will be redirected to another URL, www.lds.org in this case.
You can verify that the request was made to the proxy server but was denied (301 http response – Moved permanently) and was redirected to www.lds.org instead.
Removing Restrictions
If for some reason you need to enable a category that has been blocked in the past, remove the corresponding directory from /var/lib/squidguard/db and comment (or delete) the related acl in the squidguard.conf file.
For example, if you want to enable the domains and urls blacklisted by the anonvpn category, you would need to perform the following steps.
# rm -rf /var/lib/squidguard/db/anonvpn
And edit the squidguard.conf file as follows.
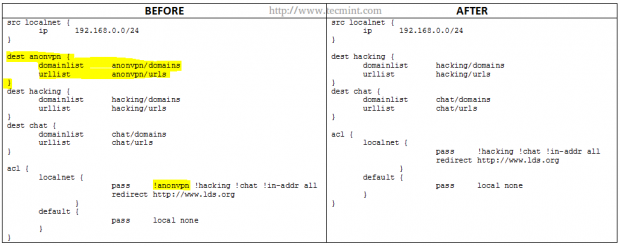
Please note that parts highlighted in yellow under BEFORE have been deleted in AFTER.
Whitelisting Specific Domains and URL’s
On occasions you may want to allow certain URLs or domains, but not an entire blacklisted directory. In that case, you should create a directory named myWhiteLists (or whatever name you choose) and insert the desired URLs and domains under /var/lib/squidguard/db/myWhiteLists in files named urls and domains, respectively.
Then, initialize the new content rules as before,
# squidGuard -C all
and modify the squidguard.conf as follows.
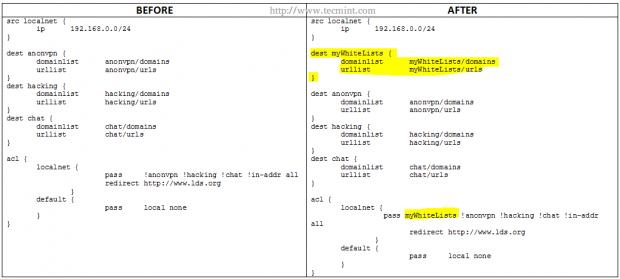
As before, the parts highlighted in yellow indicate the changes that need to be added. Note that the myWhiteLists string needs to be first in the row that starts with pass.
Finally, remember to restart Squid in order to apply changes.
Conclusion
After following the steps outlined in this tutorial you should have a powerful content filter and URL redirector working hand in hand with your Squid proxy. If you experience any issues during your installation / configuration process or have any questions or comments, you may want to refer to squidGuard’s web documentation but always feel free to drop us a line using the form below and we will get back to you as soon as possible.







