Encryption is the process of encoding files in such a way that only those who are authorized can access them. Mankind is using encryption for ages even when computers were not in existence. During the war, they would pass some kind of message that only their tribe or those who are concerned were able to understand.
Linux distribution provides a few standard encryption/decryption tools that can prove to be handy at times. Here in this article, we have covered 7 such tools with proper standard examples, which will help you to encrypt, decrypt, and password-protect your files.
If you are interested in knowing how to generate a random password from the Linux command line, read the following article:
[ You might also like: How to Generate/Encrypt/Decrypt Random Passwords in Linux ]
1. GnuPG
GnuPG stands for GNU Privacy Guard and is often called GPG which is a collection of cryptographic software. Written by GNU Project in C Programming Language. The latest stable release is 2.0.27.
In most of today’s Linux distributions, the gnupg package comes by default, if in-case it’s not installed you may apt or yum it from the repository.
$ sudo apt-get install gnupg # yum install gnupg
We have a text file (tecmint.txt) located at ~/Desktop/Tecmint/, which will be used in the examples that follows this article.
Before moving further, check the content of the text file.
$ cat ~/Desktop/Tecmint/tecmint.txt

Now encrypt the tecmint.txt file using gpg. As soon as you run the gpg command with option -c (encryption only with symmetric cipher) it will create a file tecmint.txt.gpg. You may list the content of the directory to verify.
$ gpg -c ~/Desktop/Tecmint/tecmint.txt $ ls -l ~/Desktop/Tecmint

Note: Enter Paraphrase twice to encrypt the given file. The above encryption was done with the CAST5 encryption algorithm automatically. You may specify a different algorithm optionally.
To see all the encryption algorithms present you may fire.
$ gpg --version

Now, if you want to decrypt the above-encrypted file, you may use the following command, but before we start decrypting we will first remove the original file i.e., tecmint.txt, and leave the encrypted file tecmint.txt.gpg untouched.
$ rm ~/Desktop/Tecmint/tecmint.txt $ gpg ~/Desktop/Tecmint/tecmint.txt.gpg

Note: You need to provide the same password you gave at encryption to decrypt when prompted.
2. bcrypt
bcrypt is a key derivation function that is based upon the Blowfish cipher. Blowfish cipher is not recommended since the time it was figured that the cipher algorithm can be attacked.
If you have not installed bcrypt, you may apt or yum the required package.
$ sudo apt-get install bcrypt # yum install bcrypt
Encrypt the file using bcrypt.
$ bcrypt ~/Desktop/Tecmint/tecmint.txt
As soon as you fire the above command, a new file name texmint.txt.bfe is created and the original file tecmint.txt gets replaced.
Decrypt the file using bcrypt.
$ bcrypt tecmint.txt.bfe
Note: bcrypt does not have a secure form of encryption and hence its support has been disabled at least on Debian Jessie.
3. ccrypt
Designed as a replacement for UNIX crypt, ccrypt is a utility for file and stream encryption and decryption. It uses Rijndael cypher.
If you have not installed ccrypt you may apt or yum it.
$ sudo apt-get install ccrypt # yum install ccrypt
Encrypt a file using ccrypt. It uses ccencrypt to encrypt and ccdecrypt to decrypt. It is important to notice that at encryption, the original file (tecmint.txt) is replaced by (tecmint.txt.cpt), and at decryption the encrypted file (tecmint.txt.cpt) is replaced by the original file (tecmint.txt). You may like to use the ls command to check this.
Encrypt a file.
$ ccencrypt ~/Desktop/Tecmint/tecmint.txt

Decrypt a file.
$ ccdecrypt ~/Desktop/Tecmint/tecmint.txt.cpt
Provide the same password you gave during encryption to decrypt.

4. Zip
It is one of the most famous archive formats and it is so much famous that we generally call archive files as zip files in day-to-day communication. It uses pkzip stream cipher algorithm.
If you have not installed zip you may like to apt or yum it.
$ sudo apt-get install zip # yum install zip
Create an encrypted zip file (several files grouped together) using zip.
$ zip --password mypassword tecmint.zip tecmint.txt tecmint1.1txt tecmint2.txt
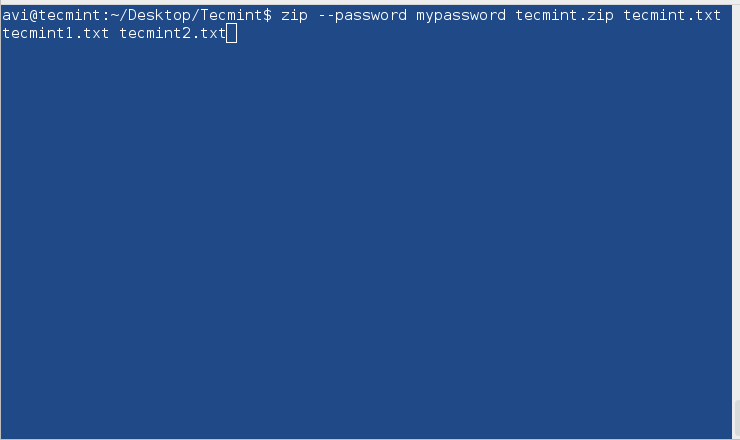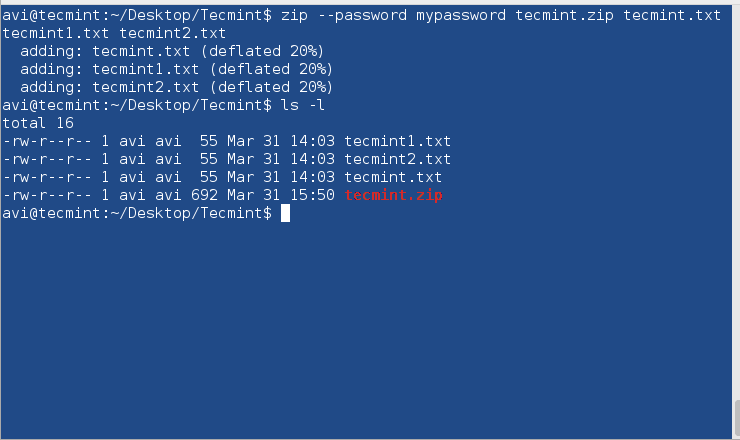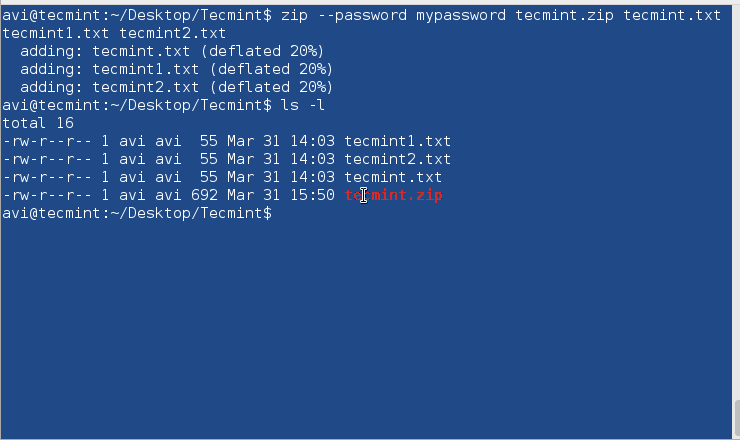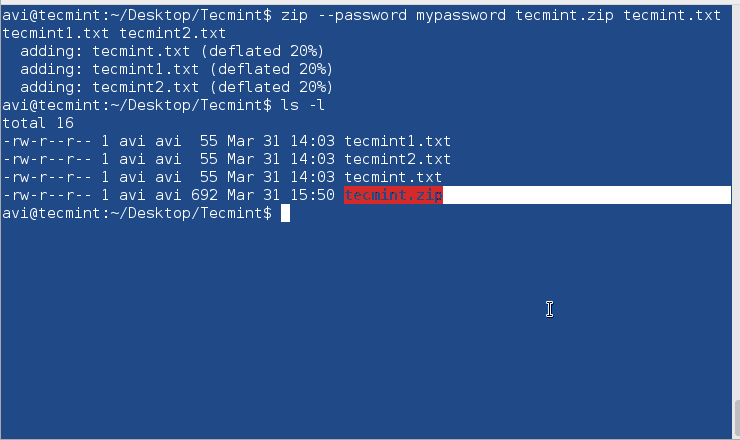
Here mypassword is the password used to encrypt it. An archive is created with the name tecmint.zip with zipped files tecmint.txt, tecmint1.txt, and tecmint2.txt.
Decrypt the password-protected zipped file using unzip.
$ unzip tecmint.zip
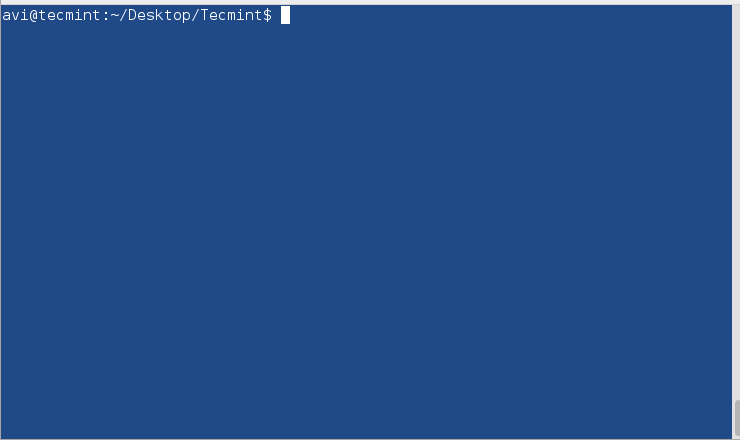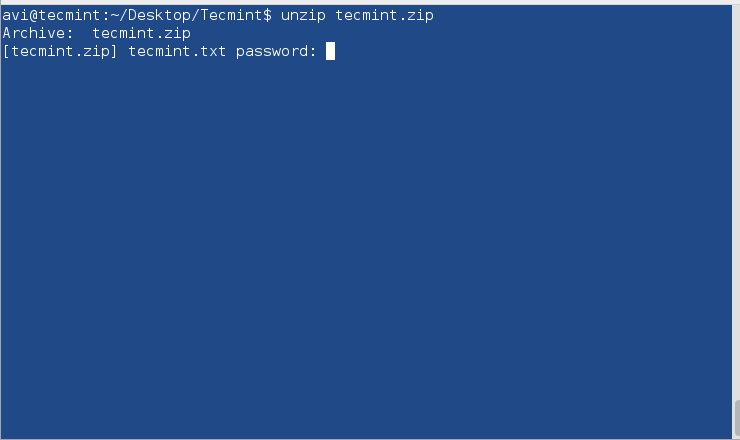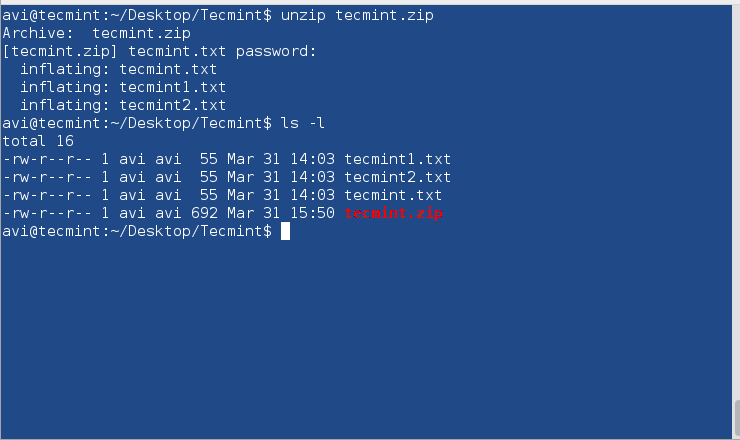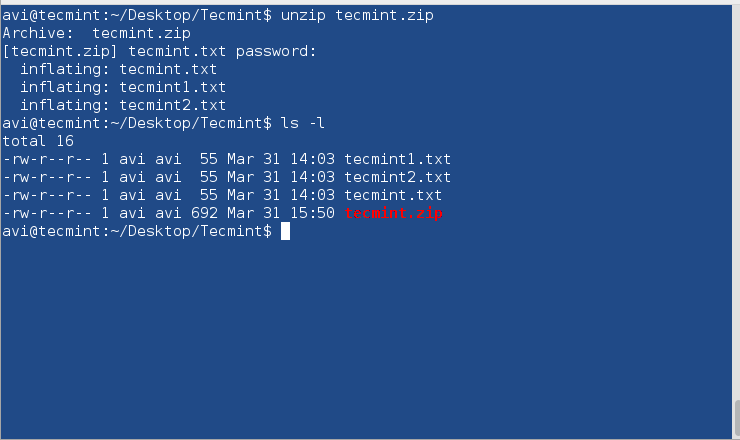
You need to provide the same password you provided at encryption.
5. Openssl
Openssl is a command line cryptographic toolkit that can be used to encrypt messages as well as files.
You may like to install openssl if it is not already installed.
$ sudo apt-get install openssl # yum install openssl
Encrypt a file using openssl encryption.
$ openssl enc -aes-256-cbc -in ~/Desktop/Tecmint/tecmint.txt -out ~/Desktop/Tecmint/tecmint.dat
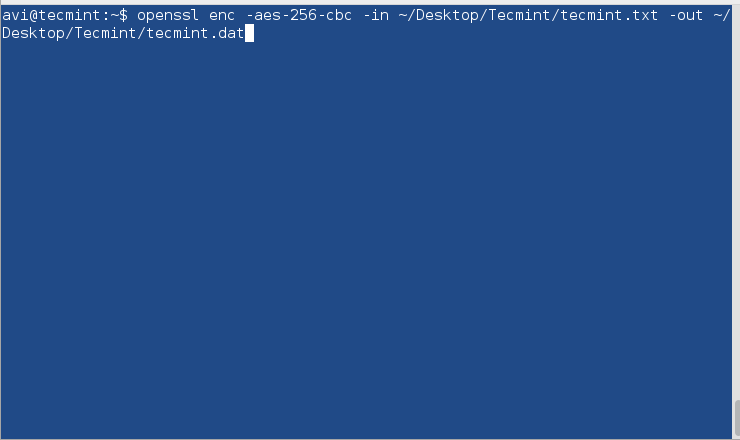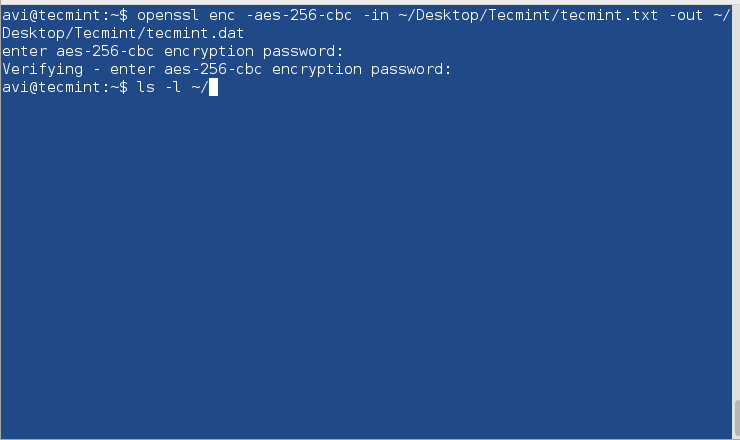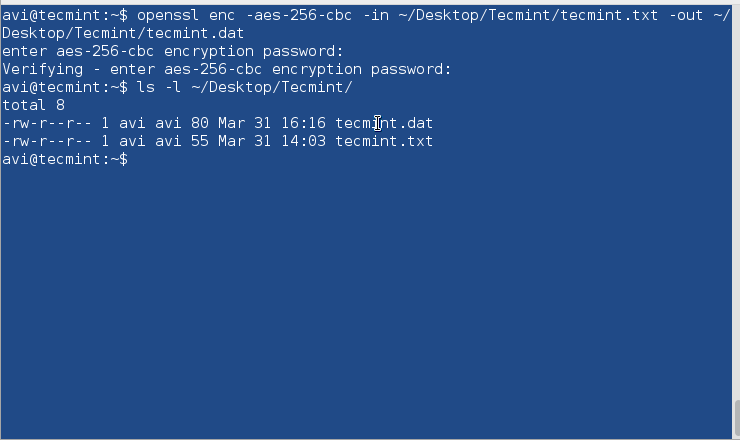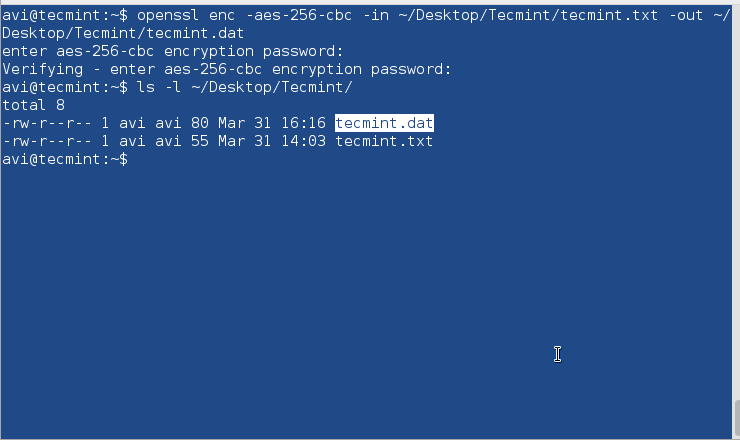
Explanation of each option used in the above command.
- enc : encryption
- -aes-256-cbc : the algorithm to be used.
- -in : full path of the file to be encrypted.
- -out : full path where it will be decrypted.
Decrypt a file using openssl.
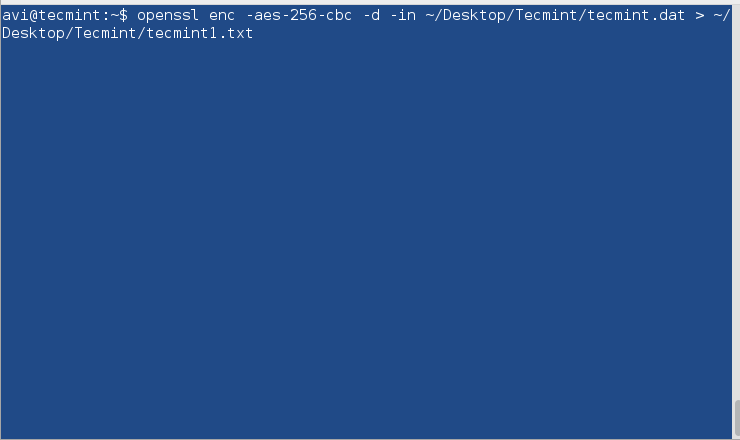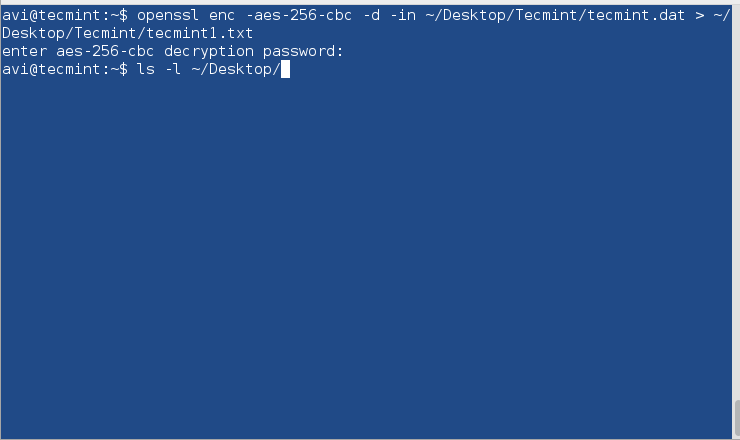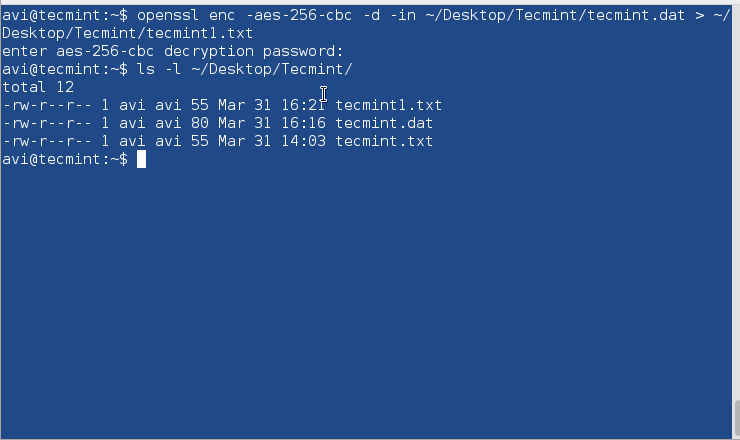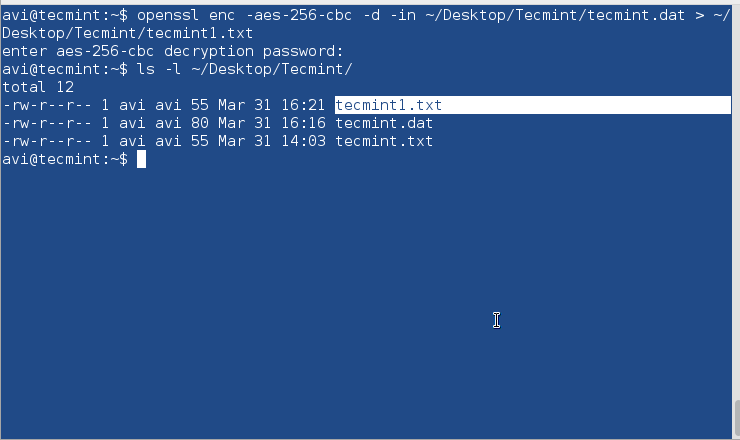
$ openssl enc -aes-256-cbc -d -in ~/Desktop/Tecmint/tecmint.dat > ~/Desktop/Tecmint/tecmint1.txt
6. 7-zip
The very famous open-source 7-zip archiver is written in C++ and is able to compress and uncompress most of the known archive file formats.
If you have not installed 7-zip you may like to apt or yum it.
$ sudo apt-get install p7zip-full # yum install p7zip-full
Compress files into zip using 7-zip and encrypt it.
$ 7za a -tzip -p -mem=AES256 tecmint.zip tecmint.txt tecmint1.txt
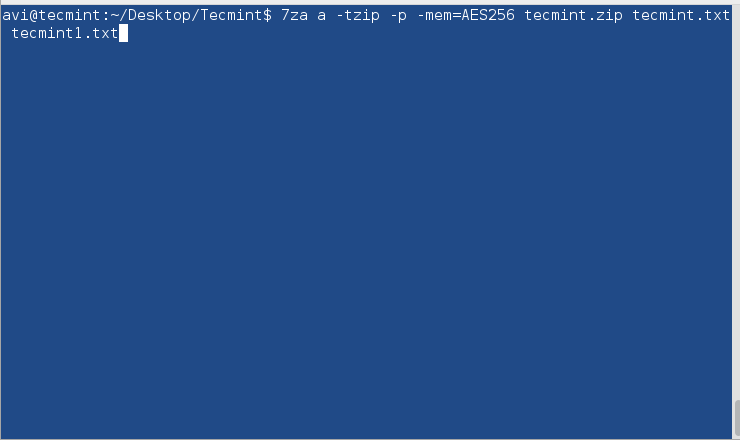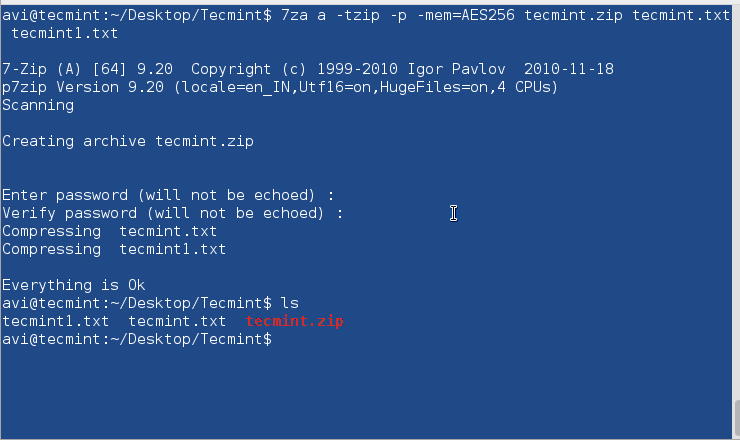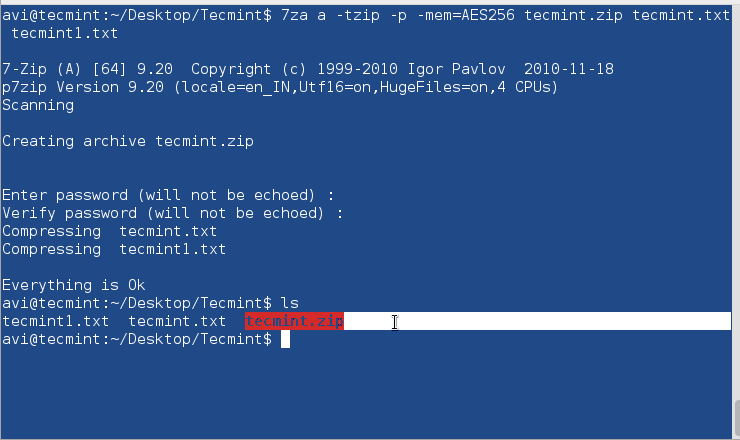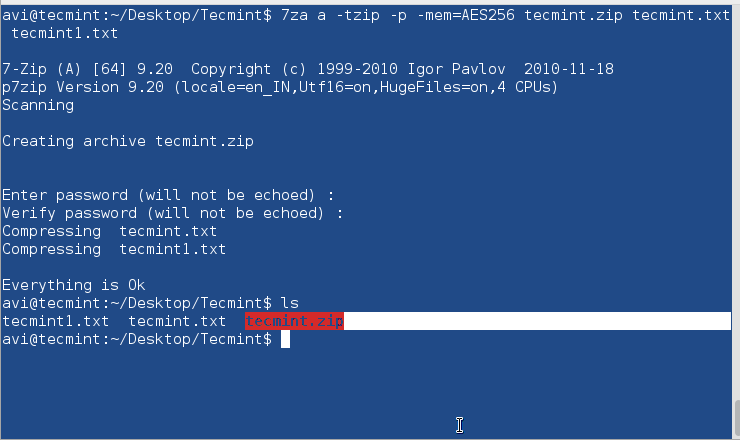
Decompress encrypted zip file using 7-zip.
$ 7za e tecmint.zip
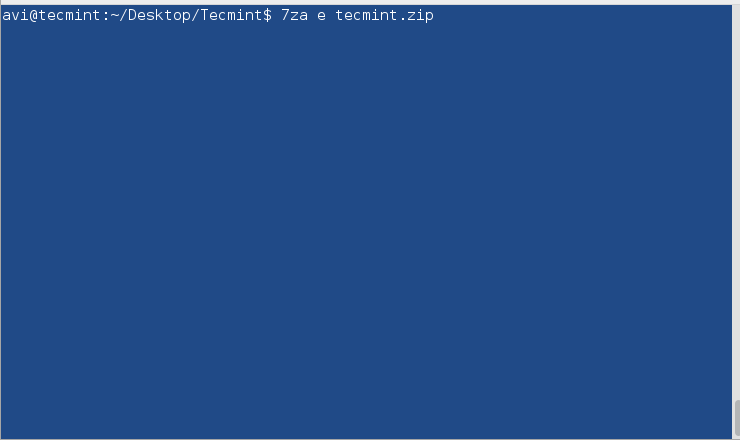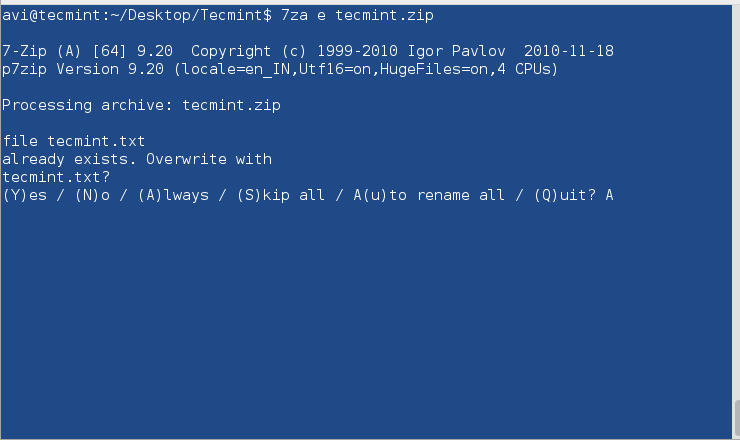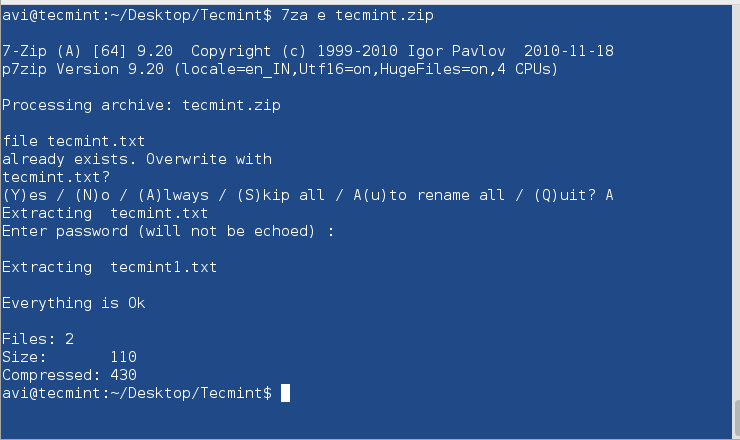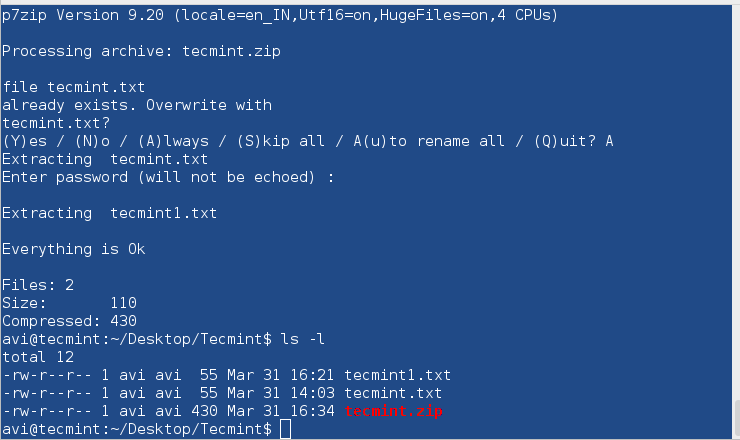
Note: Provide the same password throughout the encryption and decryption process when prompted.
All the tools we have used till now are command based. There is a GUI-based encryption tool provided by Nautilus, which will help you to encrypt/decrypt files using a Graphical interface.
7. Nautilus Encryption Utility
Steps to encrypt files in GUI using Nautilus encryption utility.
Encryption of files in GUI
1. Right-click the file you want to encrypt.
2. Select the format to zip and provide the location to save. Provide the password to encrypt as well.
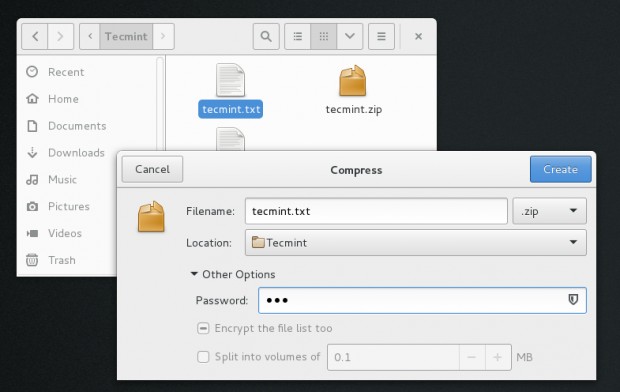
3. Notice the message – encrypted zip created successfully.
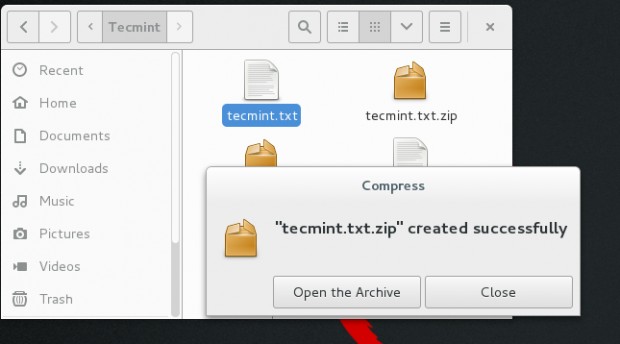
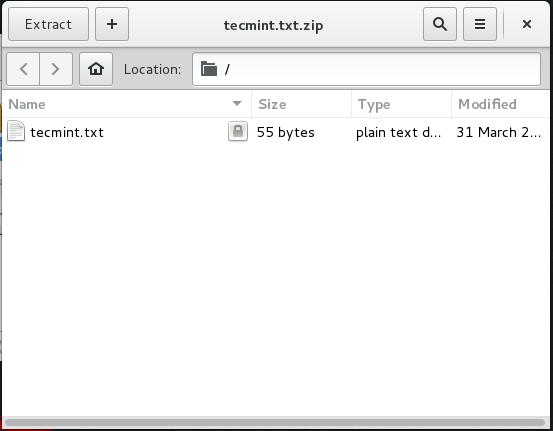
The decryption of file in GUI
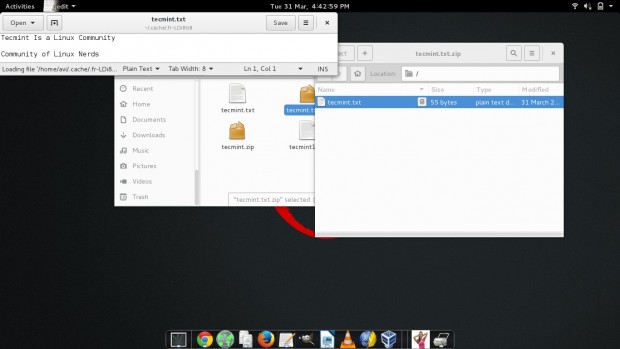
1. Try opening the zip in GUI. Notice the LOCK-ICON next to the file. It will prompt for a password, Enter it.
2. When successful, it will open the file for you.
That’s all for now. I’ll be here again with another interesting topic. Till then stay tuned and connected to Tecmint. Don’t forget to provide us with your valuable feedback in the comments below. Like and share us and help us get spread.





I have created a UNIX encryption/decryption tool using my propitiatory RSA algorithm. Currently, I am giving it to use it free for 3 months to individuals and businesses.
Easily encrypt an entire directory using encfs.
HI,
Can we pass the encryption password as an option to OpenSSL without being prompted for standard input?
I would like to implement this in a script.
You can pass the password using an environment variable, using the
-passargument:Now, in your script, you can set the environment variable, or read the password from a file.
Best regards
Thanks for sharing such a useful article. Really helps me a lot.
Yum not find out bcrypt and ccrypt?
How to download and install these packages?
@Sumit,
These packages can be installed using Nodejs, for example.
It’s absolutely hilarious that you suggest avoiding bcrypt because of cryptographic weaknesses, but then go and recommend standard ZIP file file encryption!
How to enter the encryption password while using openssl?
How to create a password protected directory without using
.httpasswdor.htaccessmethod?Very helpful article.
Any file based encryption tool makes an encrypted copy, some just pretend they didn’t by automatic deleting the unencrypted file…
Do any of these encrypt the file and not just make a copy of it? even the archiving tools seem to make a copy of the original file and encrypt it. thus leaving u with an unencrypted copy. correct me if I am wrong please.
Thanks
You forgot to say: scrypt
If we encrypt a file using the command “gpg -c filename” and use cat command to check the content, we cannot see the content without a password.
But if we use less command we can see the content. Then what is the use of it?
Hi. The 3rd tool, Ccrypt, has a typo, to decrypt a file it’s ccdecrypt instead decrypt
@Rafael,
Thanks for pointing out that typo, corrected in the writeup..
Hey Ya people!
This is funny.
It should be different and way way different.
How do we prevent somebody to copy files from our PC while we are on the Internet!
Emacs users can also use EasyPG which allows to encrypt/decrypt files with the extension .gpg
EasyPG can either use an existing GPG key or a standalone password (i.e. symmetric encryption).
See also https://www.emacswiki.org/emacs/EasyPG
@Stephane,
Thanks for the tip about EasyPG tool, never heard of this too so far, will certainly give a try right away…
That’s not 7 tools LOL.. You’re talking about integration using the same tools gezzzzzzzzzz
The article refers to bcrypt as “a key derivation function.” This shows that the author has confused bcrypt the key derivation (hash) function with bcrypt the command-line encryption program. These are two different things.
It is true that bcrypt the hash function has been found to have weaknesses of some concern. The author’s remarks about bcrypt being unsafe however do NOT apply to bcrypt the command-line encryption program.
Yeah the article is completely wrong. Stating 7 when they’re using integration which uses same tools. Bad article is you ask me.
Excellent collection, thank you very much .
Great collection!
Thanks!!! :-)
One useful addition, (at my opinion) is Veracrypt (Truecrypt successor).
https://sourceforge.net/projects/veracrypt/
Comes with an installer and it has a console and a gui version.
Also with Windows and OSX versions.
Dear All Author
Kindly share the step by step for dual installation ( window 8 & fedora 21 ) with new architecture UEFI or Legacy mode, I buy new laptop and comes this new architecture Legacy mode * UEFI Mode,
I am unable to boot both window as a Dual Boot. kindly share the tutorial from basic steps.