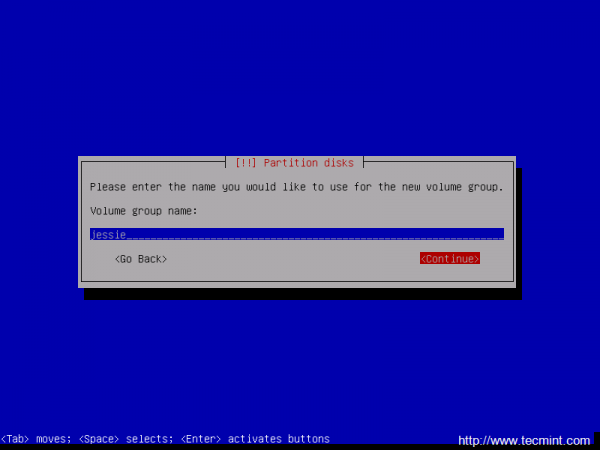
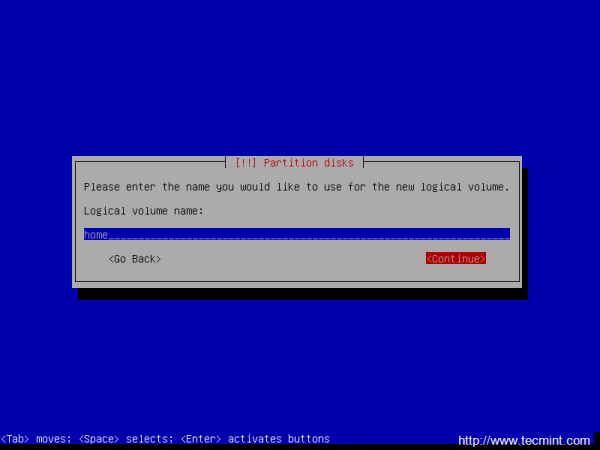
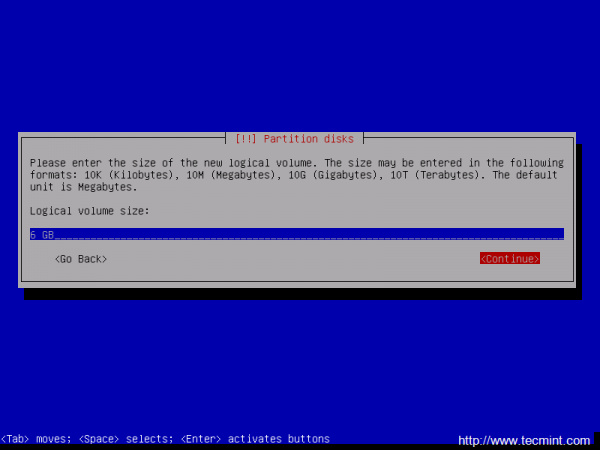
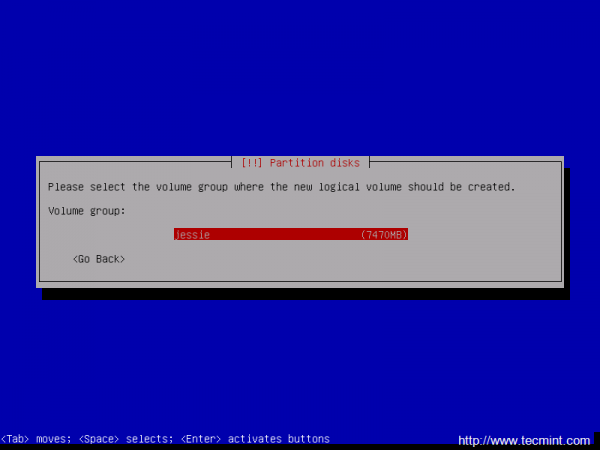
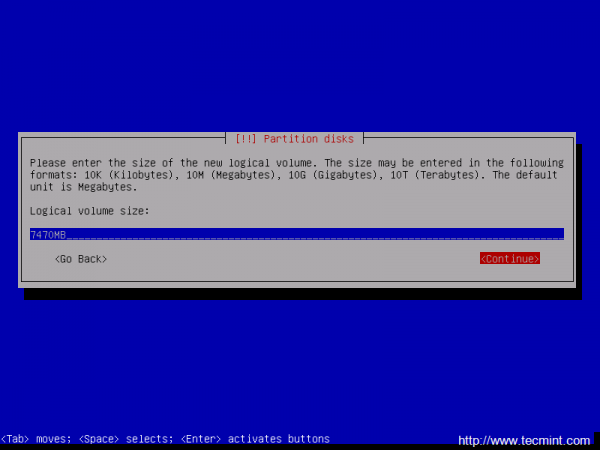
15. Now, create the Logical Volumes for /home and /var partitions. Choose Create logical volume -> Press Enter at your Volume Group name -> use the home name for the first Logical Volume -> enter a size for home Logical Volume depending on how much space you want to use for your home partition and hit Continue when you’re done.

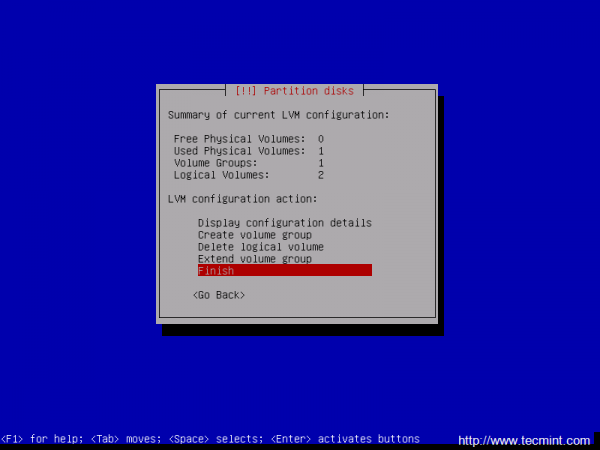
16. Next, repeat the above step in order to create the Logical Volume for /var partition and hit Finish when you’re done to go back to main Partition menu.
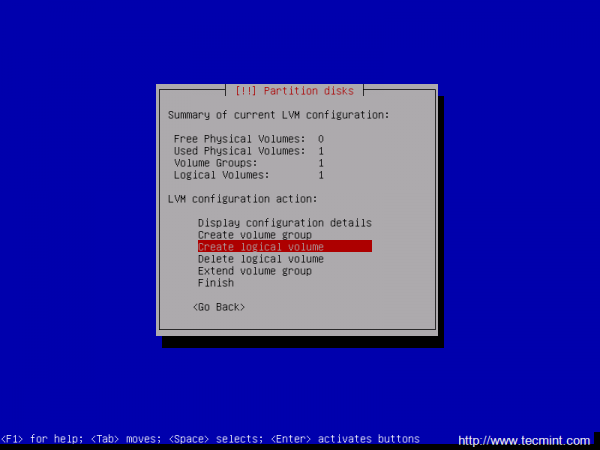

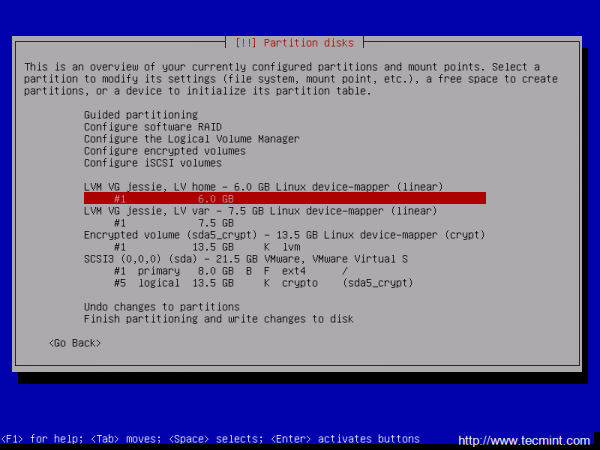
17. Once returned to the main Partition menu it’s time to configure the LVM partitions settings and mount points. Navigate to #1 home Logical Volume and configure the LVM partition with the following settings:
- Use as: Ext4 journaling file system
Mount Point: /home
- Label: home
When you finish hit the Done setting up the partition.

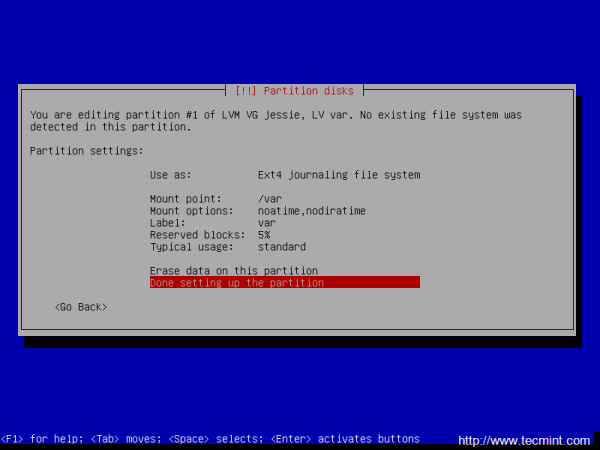
18. Repeat the above steps for #1 var Logical Volume with the following settings:
- Use as: Ext4 journaling file system
- Mount Point: /var
- Label: var
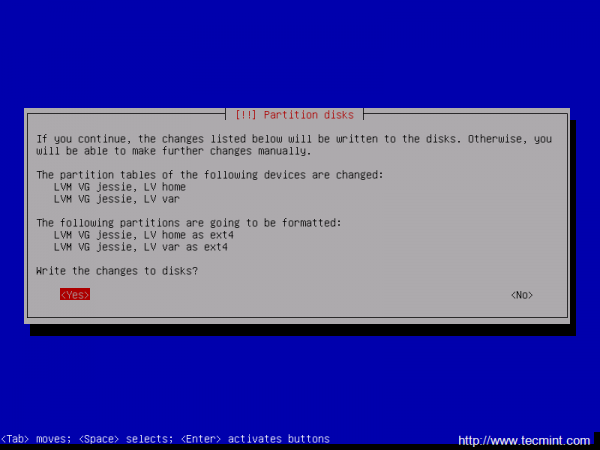
Again, after you finish setting up /var partition hit the Done setting up the partition to return to main Partition menu, review the partitions for a last time, and, if everything is in the right place, move to Finish partitioning and write changes to disk and choose No at the next prompt (Return to partitioning menu) and Yes in order to format the partitions, write changes to disk and continue with the installation process.
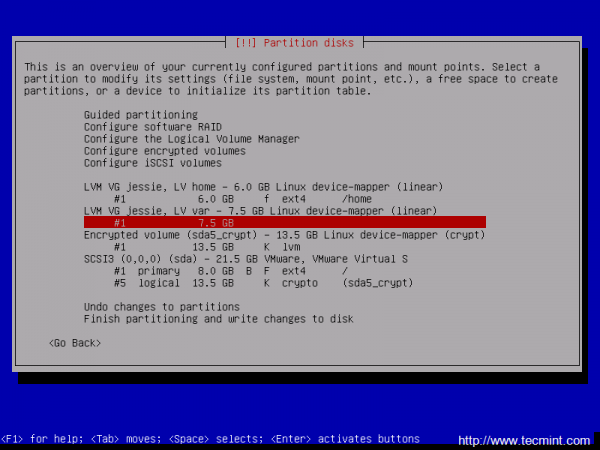
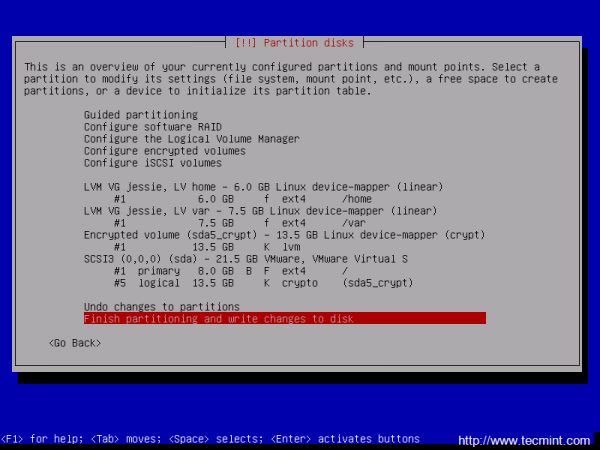
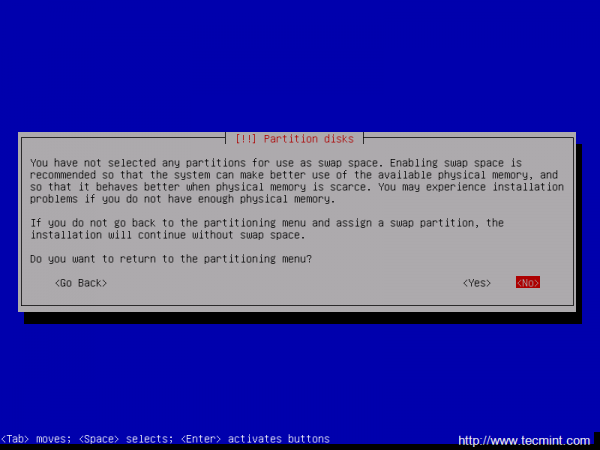
As you can see I’ve not used a swap partition for this tutorial. In case you want to use an encrypted swap partition as well, just create an extra Logical Volume with swap name and use it as Linux swap on Partition settings.
19. That’s all for the partitioning scheme in order to run LVM encrypted partitions on top of an encrypted volume.
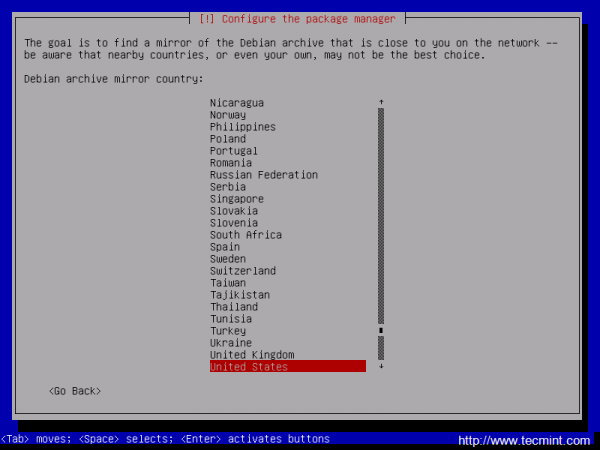
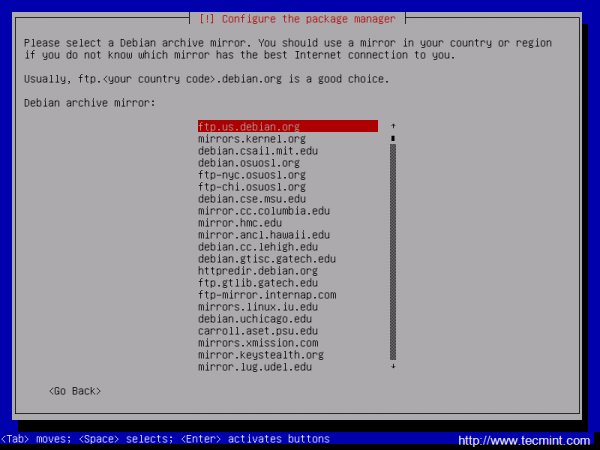
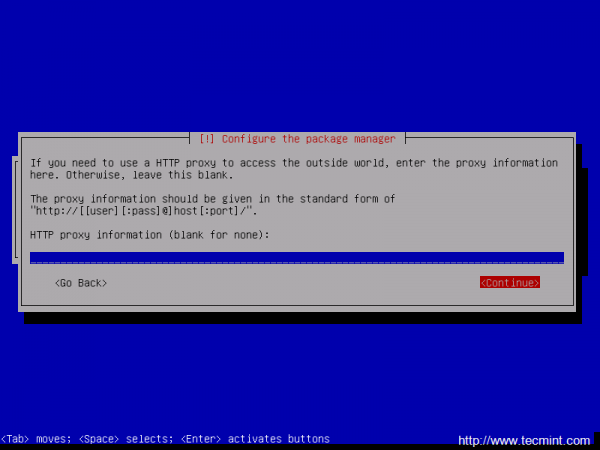
After the base system is installed, select a Debian archive mirror country for repositories. If the machine is directly connected to Internet and you do not use a proxy server to gain Internet access, hit on Continue at HTTP proxy information.
20. After the installer will configure the apt repositories a new prompt should appear demanding to participate in the package usage survey. Choose No to continue and select the software you want to install further.
Depending on the final destination of your machine, you can opt for a Graphical User Interface with your favorite Desktop environment (Gnome, Xfce, KDE, Cinnamon, MATE, LXDE) or a server configuration with no GUI.
In any case, choose standard system utilities and SSH if you want to use the machine as a server and hit Continue when you’re done.
21. After all the required packages are installed on your system, install the GRUB boot loader to your first hard disk (/dev/sda) MBR (Master Boot Record) and wait for the installation process to finish.
22. After the installation finishes hit Continue to reboot the machine. At the booting process you will be asked to enter the passphrase configured on the installation process in order to unlock the encrypted device and mount the encrypted partitions.
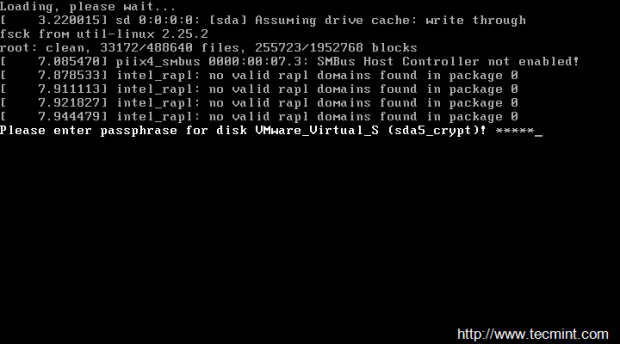
23. In order to automatically unlock and mount the encrypted /home and /var partitions during system boot up, login with root user and create a protected key on /root partition by issuing the following commands:
dd if=/dev/urandom of=cryptkey bs=512 count=1 chmod 700 cryptkey
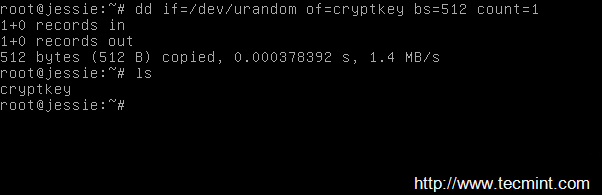
24. After the key has been created, open and edit /etc/crypttab file and replace none parameter with the absolute system path to your key as in the following screenshot:
# nano /etc/crypttab
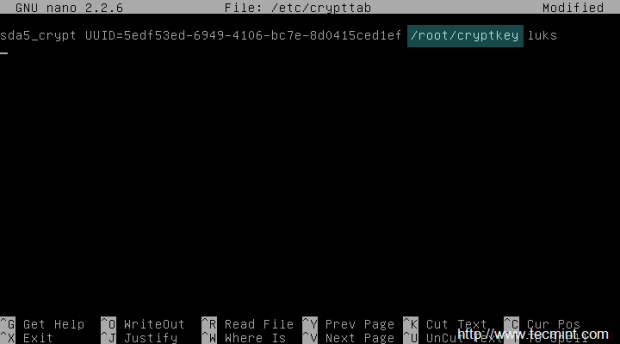
25. Next, add the key to encrypted LUKS device by issuing the following command (LUKS can support up to 8 keys or passphrase slots) and verify if the key has been added to slot number 1:
cryptsetup luksAddKey /dev/sda5 /root/cryptkey cryptsetup luksDump /dev/sda5

That’s it! On the next boot up process, the encrypted partitions will be automatically unlocked and mounted with the below decryption key. All sensitive data stored in /home and /var partitions will be highly secured in case someone gains physical access to your machine hard-drive.
Be aware that if you lose the decryption key or you forget the passphrase set during installation process the data stored onto the encrypted partitions cannot be recovered and will be forever lost, so you should take precaution and regular backup data, preferably to an encrypted device also.






hi guys
i want to know how to make passpshrase to automaticaly boot from usb.
Yeah, I’m not convinced automatic decryption works in Debian. If you issue ‘update-initramfs -u -k all’ you get the error, ‘cryptsetup: WARNING: target sdaX_crypt uses a key file, skipped.’ which will hang the system at boot.
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=776409
They’re dicking around with systemd and can’t get it sorted out so it isn’t clear if you can use a keyscript in Jessie/Stable.
>All sensitive data stored in /home and /var partitions will be highly secured in case someone gains physical access to your machine hard-drive.
I’m sorry, how exactly is it gonna be secured from anyone when we’ve just configured these partitions to be mounted automatically without asking the passphrase so anyone will be able to login on our machine and read all the data from these partitions?
That’s just a simple trick used to decrypt the partitions. I wouldn’t suggest that you should host the key on any of internal hard-disks but you can use an external drive to keep the key secure and plug the drive.
If you can boot-up and login to the console check if the / partition is present on fstab (i’m guessing the root partition is not encrypted). Then update the initramfs image with the command ‘update-initramfs -u’
Hi, after “update-initramfs -u -k all” the system won’t boot anymore with the error “Unable to find LVM volume hostname-vg/root”. Without that command the passphrase as still asked at boot. Do I need to add anything to /etc/fstab?
Any other suggestion?
put the key on usb stick :)
After step 25 (add the key to encrypted LUKS device and enter the passphrase) the key is not be added to the slot, but I get a message “Failed to open key file”.
All previous steps went flawless.
What went wrong?
Check permissions on /root/cryptkey file.
Hi,
After the last step, to make the system use the key file, I had to :
update-initramfs -u -k all
WIthout this command, the passphrase was still asked at boot time.
But I’m really wondering… how is it secure to store the key on disk, in the case someone get physical access to your hard drive? If I do this on a netbook, and someone steal it, will he be able to unlock the crypted volume after he found this key file??
Thanks for the tutorial!
Mate, you describe the creation of dm-crypt containers, which are not really LUKS. Try changing the pasword on the volume you create (a trivial operation for LUKS), and let us know how it worked.
“All sensitive data stored in /home and /var partitions will be highly secured in case someone gains physical access to your machine hard-drive.”
–> huummm , seriously ?
@Lemoidului,
Yes, what’s wrong here? /home contains important user data and /var contains important server logs, these two partitions needs to be secured..Instead finding out errors in the article, appreciate the author for his work hard..
IMHO, having a encrypted partition with the encryption key stored in a clear text partition by its side, is useless. A false sense of security.
Couldn’t agree more. I can decrypt your drives in 60 seconds if you store decryption key that way.
This is just a very simple and convenient trick to automatically decrypt and load the encrypted volume in case you don’t have any physical access to the machine or it’s impossible to access or tamper with the boot sequence in order to manually supply the passphrase.
@Chris: Check if the key has been added to the encrypted device slot by issuing cryptsetup luksDump command.Also, and verify the content of /etc/crypttab file and ensure that the correct key with absolute path has been added.
” Failed to open key file. ”
So whan next?
Sorry if I missed something, but… what’s the point of having a encrypted partition and storing the encryption password in a unencrypted partition?