The Internet is a scary place these days. Almost daily, a new zero day, security breach, or ransomware occurs leaving many people wondering if it is possible to secure their systems.
Many organizations spends hundreds of thousands, if not millions, of dollars trying to install the latest and greatest security solutions to protect their infrastructure and data. Home user’s though are at a monetary disadvantage. Investing even a hundred dollars into a dedicated firewall is often beyond the scope of most home networks.
Thankfully, there are dedicated projects in the open source community that are making great strides in the home user security solutions arena. Projects like IPfire, Snort, Squid, and pfSense all provide enterprise level security at commodity prices!
PfSense is a FreeBSD based open source firewall solution. The distribution is free to install on one’s own equipment or the company behind pfSense, NetGate, sells pre-configured firewall appliances.
The required hardware for pfSense is very minimal and typically an older home tower can easily be re-purposed into a dedicated pfSense Firewall. For those looking to build or purchase a more capable system to run more of pfSense’s advanced features, there are some suggested hardware minimums:
Hardware Minimums
- 500 mhz CPU
- 1 GB of RAM
- 4GB of storage
- 2 network interface cards
Suggested Hardware
- 1GHz CPU
- 1 GB of RAM
- 4GB of storage
- 2 or more PCI-e network interface cards.
Serious Home User Hardware Suggestions (and Enterprises)
In the event that a home user would like to enable many of the extra features and functions of pfSense such as Snort, Anti-Virus scanning, DNS blacklisting, web content filtering, etc the recommended hardware becomes a little more involved.
To support the extra software packages on the pfSense firewall, it is recommended that the following hardware be provided to pfSense:
- Modern multi-core CPU running at least 2.0 GHz
- 4GB+ of RAM
- 10GB+ of HD space
- 2 or more Intel PCI-e network interface cards
Installation of pfSense 2.4.4
In this section, we will see the installation of pfSense 2.4.4 (latest version at the time of writing this article).
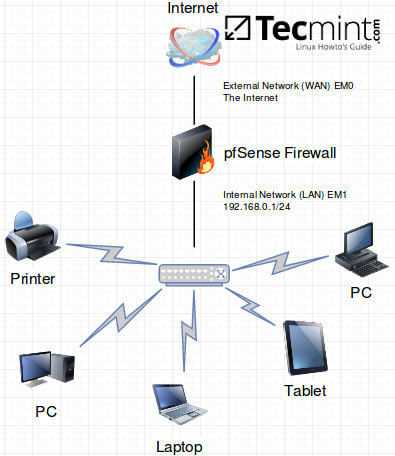
The Lab Setup
pfSense is often frustrating for users new to firewalls. The default behavior for many firewalls is to block everything, good or bad. This is great from a security standpoint but not from a usability standpoint. Before starting into the installation, it is important to conceptualize the end goal before beginning the configurations.
Downloading pfSense
Regardless of which hardware is chosen, installing pfSense to the hardware is a straightforward process but does require the user to pay close attention to which network interface ports will be used for which purpose (LAN, WAN, Wireless, etc).
Part of the installation process will involve prompting the user to begin configuring LAN and WAN interfaces. The author suggests only plugging in the WAN interface until pfSense has been configured and then proceed to finish the installation by plugging in the LAN interface.
The first step is to obtain the pfSense software from https://www.pfsense.org/download/. There are a couple of different options available depending on the device and installation method but this guide will utilize the ‘AMD64 CD (ISO) Installer’.
Using the drop down menu’s on the link provided earlier, select an appropriate mirror to download the file.
Once the installer has been downloaded, it can either be burned to a CD or it can be copied to a USB drive with the ‘dd’ tool included in most Linux distributions.
The next process is to write the ISO to a USB drive to boot the installer. To accomplish this, use the ‘dd’ tool within Linux. First, the disk name needs to be located with ‘lsblk’ though.
$ lsblk
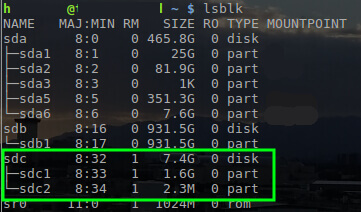
With the name of the USB drive determined as ‘/dev/sdc’, the pfSense ISO can be written to the drive with the ‘dd’ tool.
$ gunzip ~/Downloads/pfSense-CE-2.4.4-RELEASE-p1-amd64.iso.gz $ dd if=~/Downloads/pfSense-CE-2.4.4-RELEASE-p1-amd64.iso of=/dev/sdc
Important: The above command requires root privileges so utilize ‘sudo’ or login as the root user to run the command. Also this command will REMOVE EVERYTHING on the USB drive. Be sure to backup needed data.
Installation of pfSense
Once ‘dd’ has finished writing to the USB drive or the CD has been burnt, place the media into the computer that will be setup as the pfSense firewall. Boot that computer to that media and the following screen will be presented.
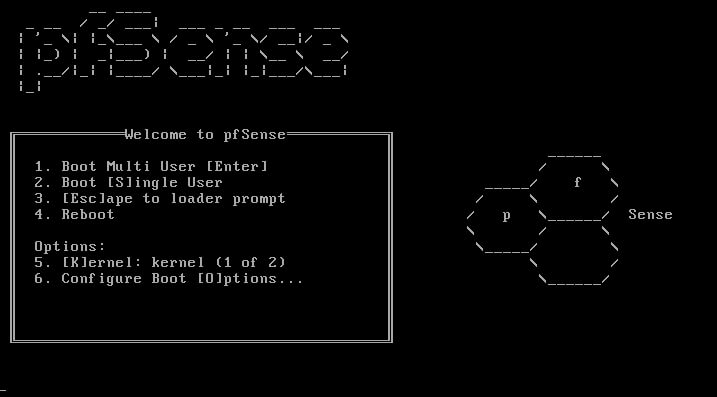
At this screen, either allow the timer to run out or select 1 to proceed booting into the installer environment. Once the installer finishes booting, the system will prompt for any changes desired in the keyboard layout. If everything shows in a native language, simply click on ‘Accept these Settings’.
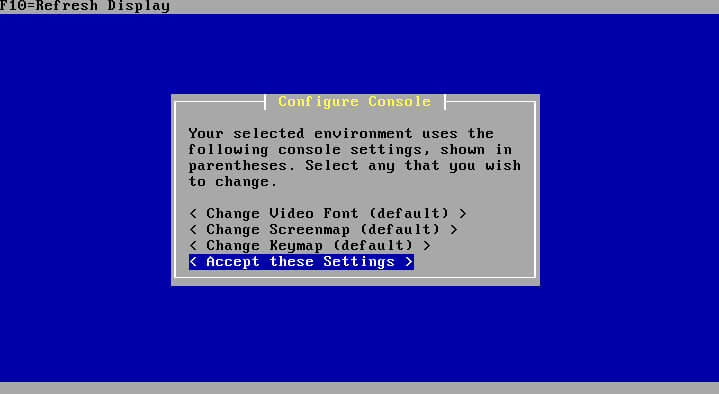
The next screen will provide the user with the option of a ‘Quick/Easy Install’ or more advanced install options. For the purposes of this guide, it is suggested to simply use the ‘Quick/Easy Install’ option.
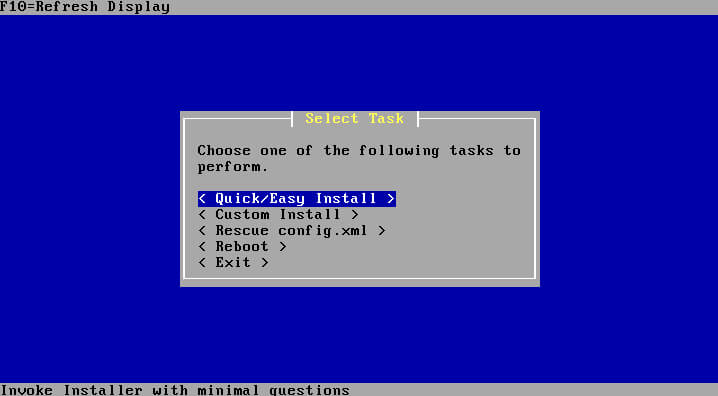
The next screen will simply confirm that the user desires to use the ‘Quick/Easy Install’ method which won’t ask as many questions during the installation.
The first question that is likely to be presented will ask about which kernel to install. Again, it is suggested that the ‘Standard Kernel’ be installed for most users.
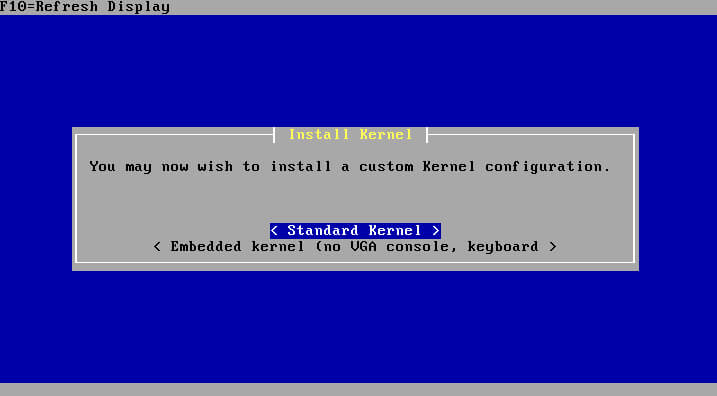
When the installer has finished this stage, it will prompt for a reboot. Be sure to remove the installation media as well so the machine doesn’t boot back into the installer.
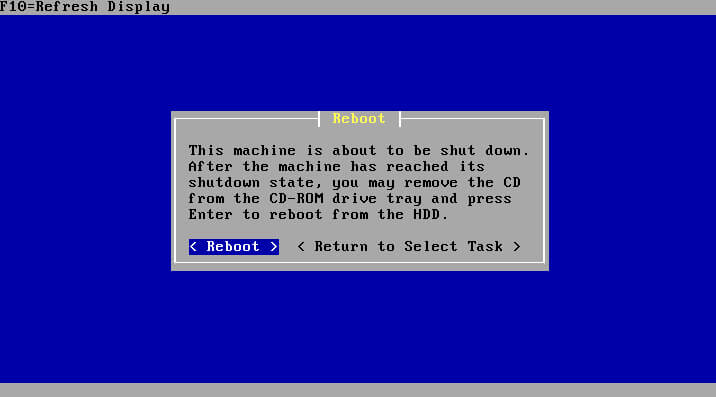
pfSense Configuration
After the reboot, and the removal of the CD/USB media, pfSense will reboot into the newly installed operating system. By default, pfSense will pick an interface to set-up as the WAN interface with DHCP and leave the LAN interface unconfigured.
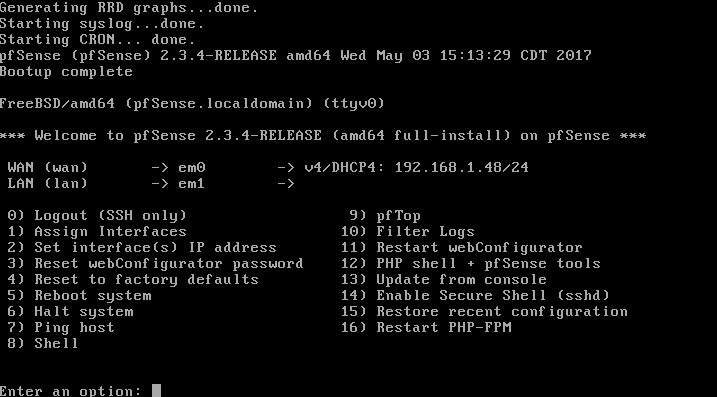
While pfSense does have a web based graphical configuration system, it is only running on the LAN side of the firewall but at the moment, the LAN side will be unconfigured. The first thing to do would be to set an IP address on the LAN interface.
To do this follow these steps:
- Take note of which interface name is the WAN interface (em0 above).
- Enter ‘1’ and press the ‘Enter’ key.
- Type ‘n’ and press the ‘Enter’ key when asked about VLANs.
- Type in the interface name recorded in step one when prompted for the WAN interface or change to the proper interface now. Again this example, ‘em0’ is the WAN interface as it will be the interface facing the Internet.
- The next prompt will ask for the LAN interface, again type the proper interface name and hit the ‘Enter’ key. In this install, ‘em1’ is the LAN interface.
- pfSense will continue to ask for more interfaces if they are available but if all interfaces have been assigned, simply hit the ‘Enter’ key again.
- pfSense will now prompt to ensure that the interfaces are assigned properly.
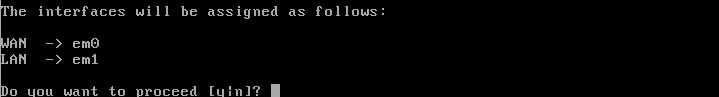
- If the interfaces are correct, type ‘y’ and hit the ‘Enter’ key.
The next step will be to assign the interfaces the proper IP configuration. After pfSense returns to the main screen, type ‘2’ and hit the ‘Enter’ key. (Be sure to keep track of the interface names assigned to the WAN and LAN interfaces).
*NOTE* For this install the WAN interface can use DHCP without any problems but there may be instances where a static address would be required. The process for configuring a static interface on the WAN would be the same as the LAN interface that is about to be configured.
Type ‘2’ again when prompted for which interface to set IP information. Again 2 is the LAN interface in this walk through.
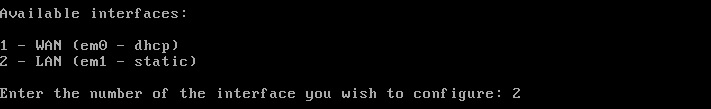
When prompted, type the IPv4 address desired for this interface and hit the ‘Enter’ key. This address should not be in use anywhere else on the network and will likely become the default gateway for the hosts that will be plugged into this interface.
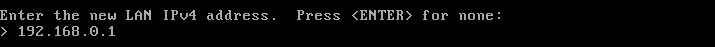
The next prompt will ask for the subnet mask in what is known as prefix mask format. For this example network a simple /24 or 255.255.255.0 will be used. Hit the ‘Enter’ key when done.
The next question will ask about an ‘Upstream IPv4 Gateway’. Since the LAN interface is currently be configured, simply hit the ‘Enter’ key.
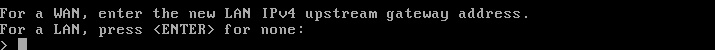
The next prompt will ask to configure IPv6 on the LAN interface. This guide is simply using IPv4 but should the environment require IPv6, it can be configured now. Otherwise, simply hitting the ‘Enter’ key will continue.
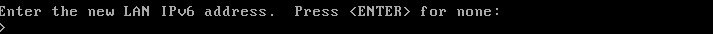
The next question will ask about starting the DHCP server on the LAN interface. Most home users will need to enable this feature. Again this may need to be adjusted depending on the environment.
This guide assumes that the user will want the firewall to provide DHCP services and will allocate 51 addresses for other computers to obtain an IP address from the pfSense device.
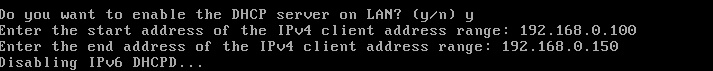
The next question will ask to revert pfSense’s web tool to the HTTP protocol. It is strongly encouraged NOT to do this as the HTTPS protocol will provide some level of security to prevent disclosure of the admin password for the web configuration tool.
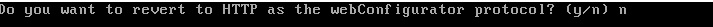
Once the user hits ‘Enter’, pfSense will save the interface changes and start the DHCP services on the LAN interface.
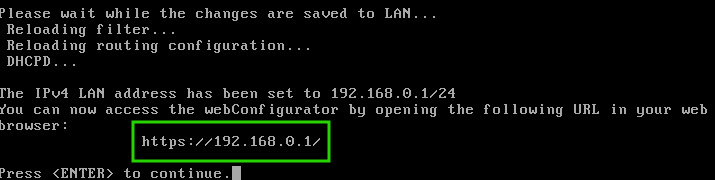
Notice that pfSense will provide the web address to access the web configuration tool via a computer plugged in on the LAN side of the firewall device. This concludes the basic configuration steps to make the firewall device ready for more configurations and rules.
The web interface is accessed through a web browser by navigating to the LAN interface’s IP address.
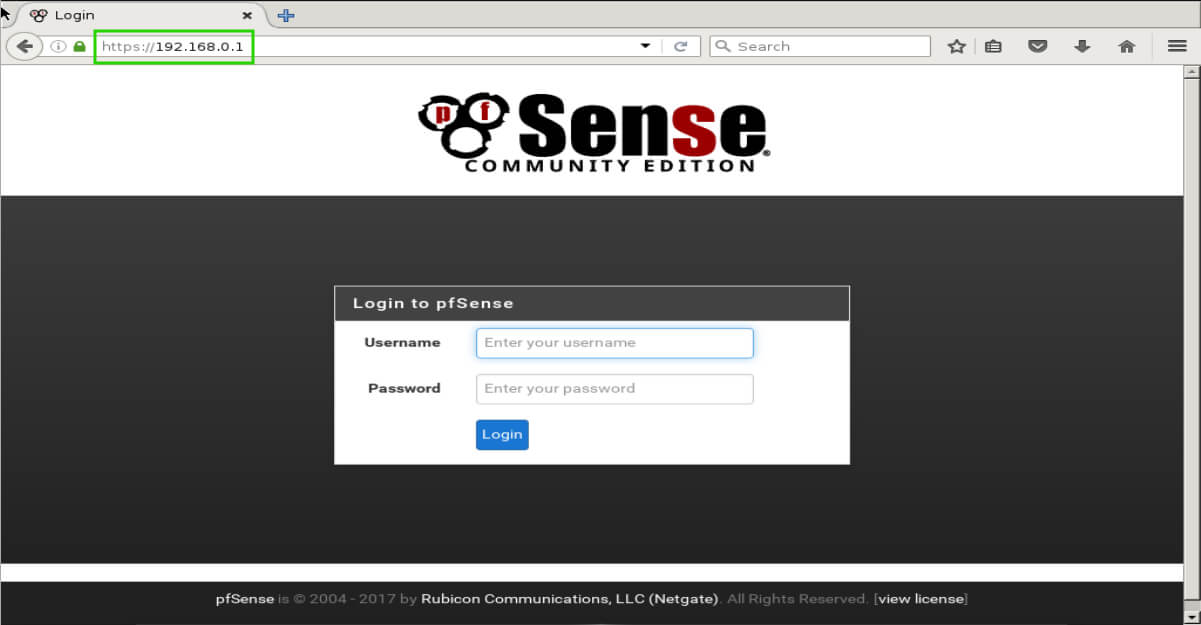
The default information for pfSense at the time of this writing is as follows:
Username: admin Password: pfsense
After a successful login through the web interface for the first time, pfSense will run through an initial setup to reset the admin password.
The first prompt is for a registration to pfSense Gold Subscription which has benefits such as automatic configuration backup, access to the pfSense training materials, and periodic virtual meetings with pfSense developers. Purchasing of a Gold subscription isn’t required and the step can be skipped if desired.
The following step will prompt the user for more configuration information for the firewall such as hostname, domain name (if applicable), and DNS servers.
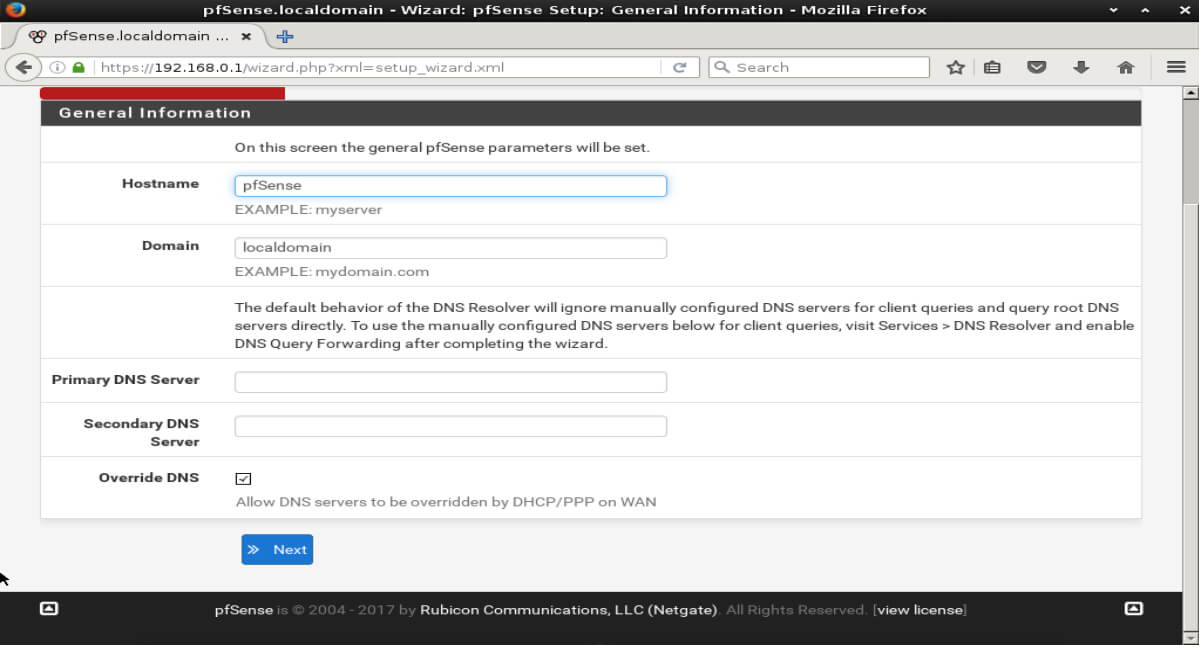
The next prompt will be to configured Network Time Protocol, NTP. The default options can be left unless different time servers are desired.
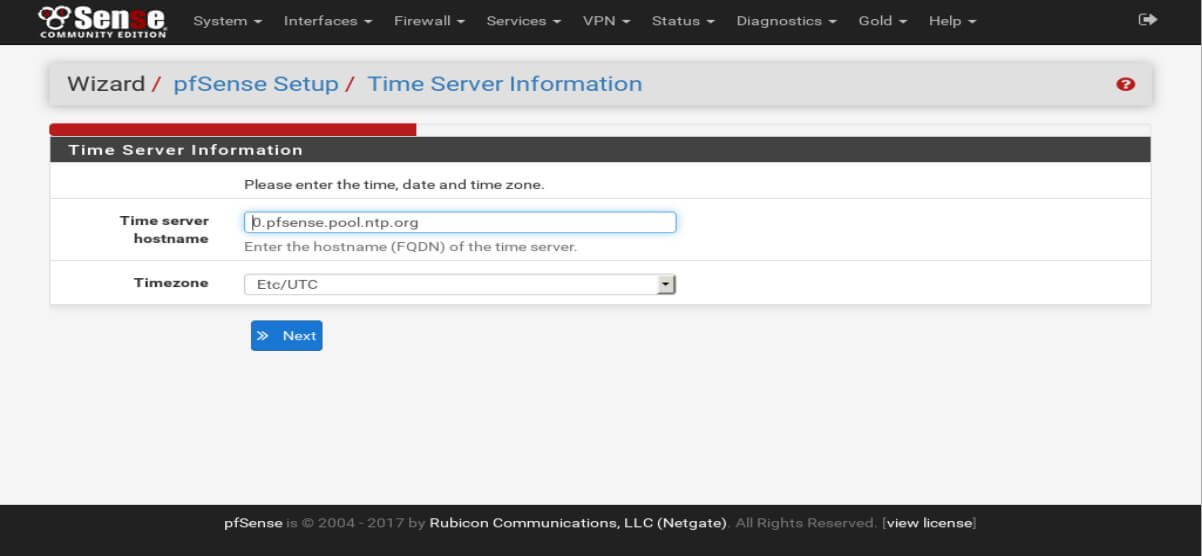
After setting up NTP, the pfSense installation wizard will prompt the user to configure the WAN interface. pfSense supports multiple methods for configuring the WAN interface.
The default for most home users is to use DHCP. DHCP from the user’s internet service provider is the most common method for obtaining the necessary IP configuration.
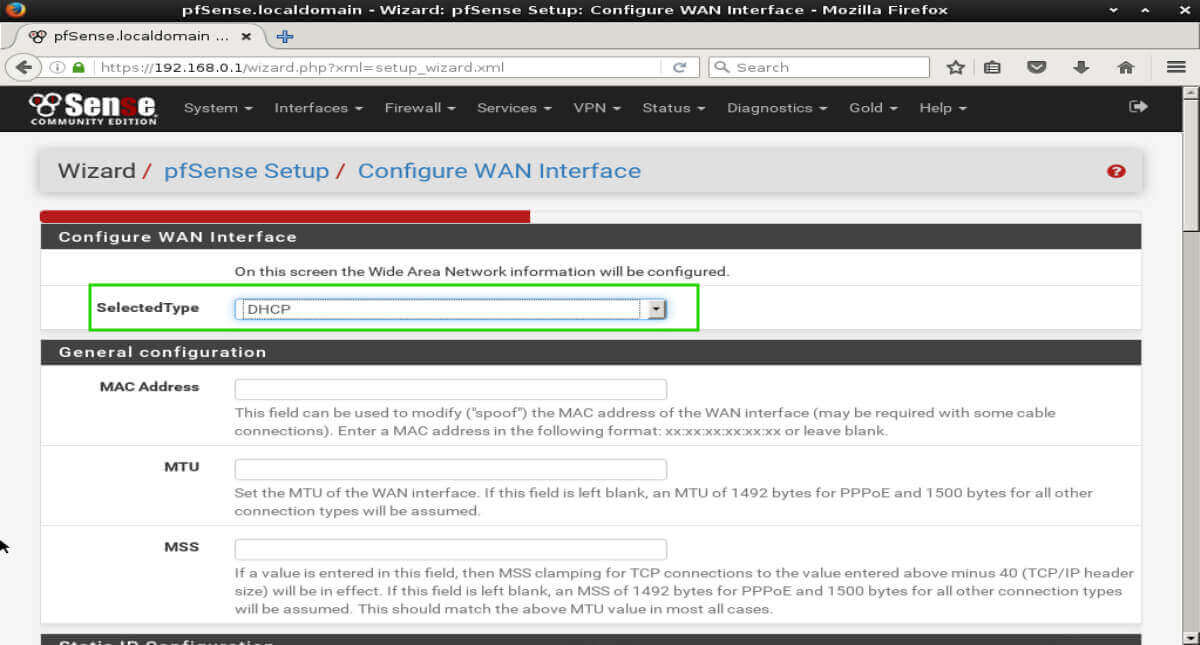
The next step will prompt for configuration of the LAN interface. If the user is connected to the web interface, the LAN interface has likely already been configured.
However, if the LAN interface needs to be changed, this step would allow for changes to be made. Make sure to remember what the LAN IP address is set to as this is how the
administrator will access the web interface!
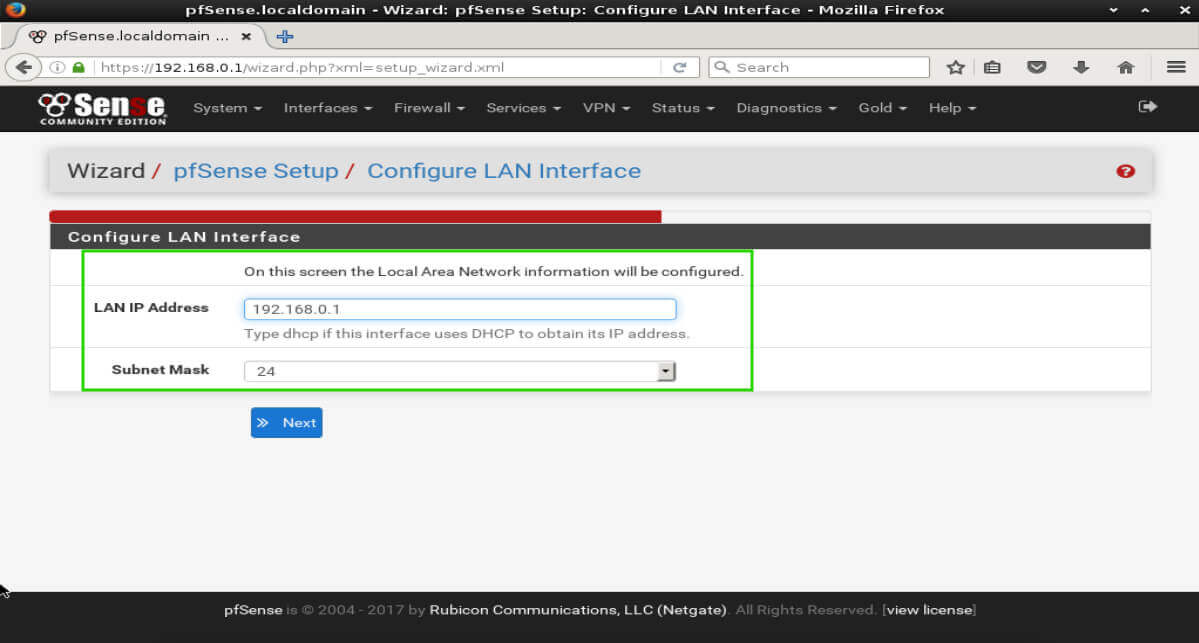
As with all things in the security world, default passwords represent an extreme security risk. The next page will prompt the administrator to change the default password for the ‘admin’ user to the pfSense web interface.
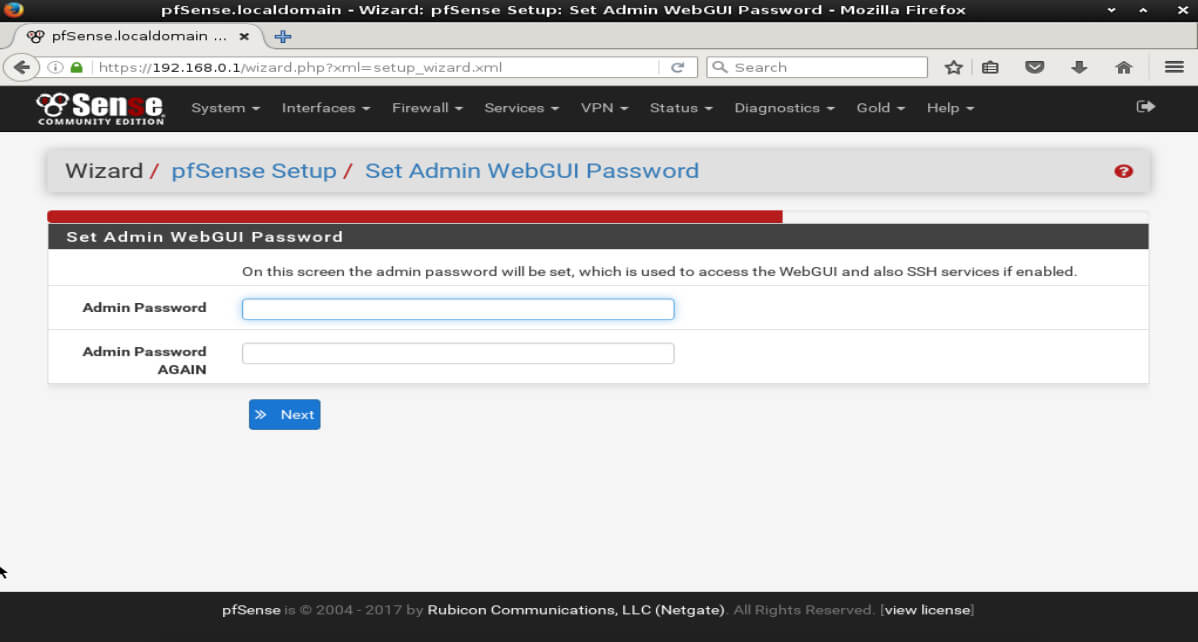
The final step involves restarting pfSense with the new configurations. Simply click the ‘Reload’ button.
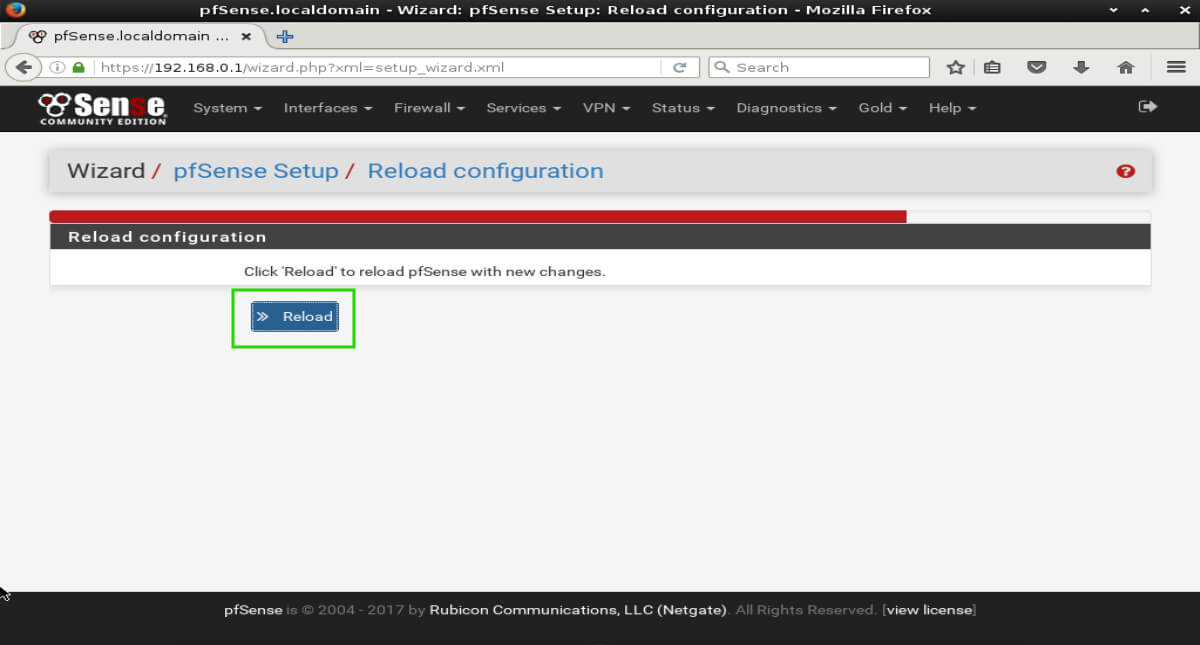
After pfSense reloads, it will present the user with a final screen before logging into the full web interface. Simply click the second ‘Click Here’ to log into the full web interface.
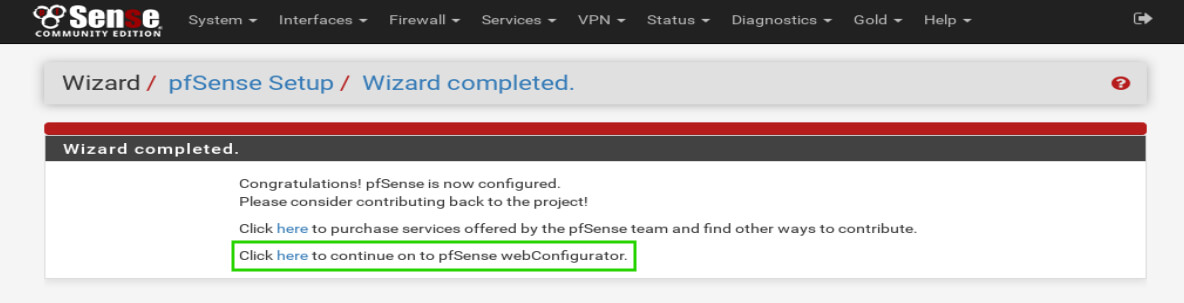
At last pfSense is up and ready to have rules configured!
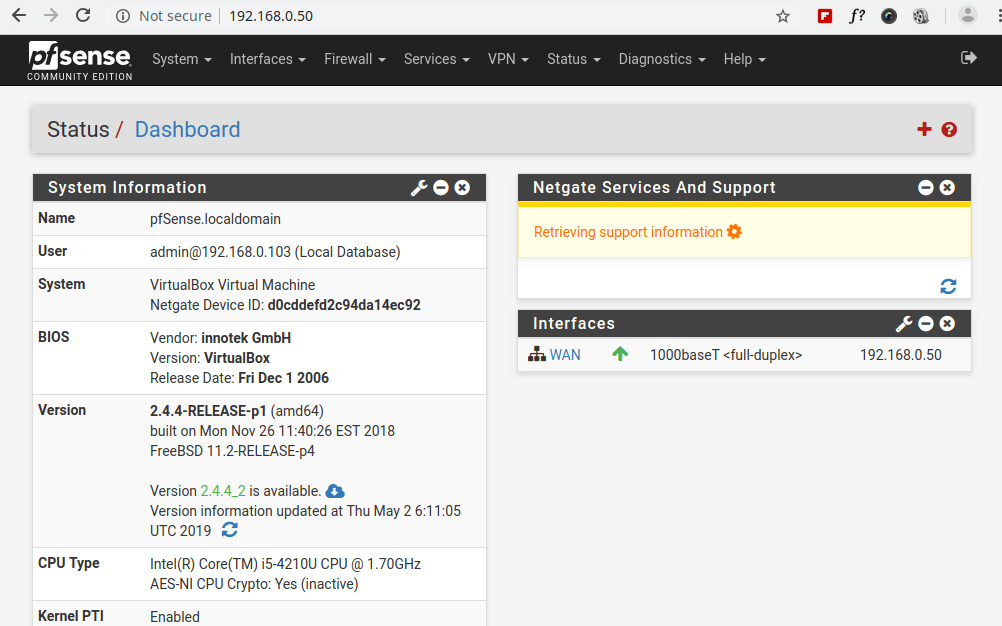
Now that pfSense is up and running, the administrator will need to go through and create rules to allow the appropriate traffic through the firewall. It should be noted that pfSense has a default allow all rule. For security sake, this should be changed but this is again an administrator’s decision.
Read Also : Install and Configure pfBlockerNg for DNS Black Listing in pfSense Firewall
Thank you for reading through this TecMint article on pfSense installation! Stay tuned for future articles on configuring some of the more advanced options available in pfSense.





Hi,
Very nice tutorial. This helps me a lot in order to test the pfsense since I was trying to replace my DDWRT router.
Could you guys do a video on PFsense as well please.
Chidi,
If you followed this guide, you will have installed PFsense over your CentOS installation….
You would have to reinstall CentOS in order to get it back.
Hi, I have finished configuring pfsense on my system, but whenever i tried to reboot my system it tends to return to pfsense.
Please how do i return to CENTOS ?
Hi Rob, nice tutorial i just discovered. PfSense can not display my Wan IP. therefore, I’m not able to to display the web configuration page through https://10.10.10.9 to enter firewall rules. Can u help me?
I am on virtualbox with the both wan and LAN interfaces named as pcn0 for WAN and pcn1 for LAN.
Please, help.
Moande,
The web interface is done through the LAN interface not the WAN interface. If you’re using VirtualBox you’ll have to plug another VM into the LAN side network to access the LAN side of the PFsense box.
Hello,
Nice tutorial. I want to know the steps to be followed if I want to configure pfsense between my router (TP-Link) and switch (CISCO). How can i do so? ip that i am getting from router is like 192.168.0.XX. Please guide me through the configuration for the same.
Thank you
Ankit,
There’s a little bit more planning needed to do this correctly but the high level would look something like this:
{Internet} ———> [TP Link Router] ———> WAN Port — (PFSense) – LAN Port ——–> {Cisco Switch}
Now that being said, there are a lot of design considerations that would need to be addressed here. Without more knowledge about what the end goal is and how the internal network will be setup, I can’t really provide step-by-step instructions. Items like NAT, DHCP, DNS resolution, etc all become issues here.
I have 2.3.4-p7. After I did a Factory reset, System and packages are not updating. It says ‘Unable to update‘. Hence now I cannot install other packages. please help.
Pravin
India.
Pravin,
I had that issue about a month ago after a PFsense upgrade. After a reboot the system was able to upgrade/install items as normal. May need to give the box one more restart when possible.
Hi, I have installed pfSense for physical system, but how to configure and set firewall setting, you can help me.
Mamallan,
Thanks for the post. What exactly are you looking to configure? Tecmint has a guide on configuring PFblockerNG here: https://www.tecmint.com/install-configure-pfblockerng-dns-black-listing-in-pfsense/
Dear Sir,
I have a wan IP i.e static 192.168.0.247 and my LAN network is 192.168.3.1/24 .
My wan interface always show up but when i check gateway it is showing offline and internet is not working
Please guide me
Aman,
Are you sure that’s the right IP address for your WAN interface? Most WAN interfaces should be using public IP addressing often provided from the ISP. If that is indeed the proper address, have you created any firewall rules that may be blocking traffic?
Hi! I’m student, I have homework about install PFSense in Centos 6.7 and I would like to “How to configuration of PFsense Fire wall 2.4.1”.
Can you help me.
Ken,
I’m not sure what you mean. PFsense is a standalone firewall distribution. You can’t install it inside of CentOS unless you mean as a virtual machine? Could you elaborate on what you’re trying to accomplish?
I am beginner and I have tested Pfsense 2.3.4 on vbox. Pfsense have 2 NIC’s, one is WAN that is dhcp, other one is LAN is static. I use guest OS on vbox and connect to pfsense. pfsense access internet, but Guest OS didn’t get internet but ping to 8.8.8.8 is ok and ping to http://www.google.com not ok. nslookup show
how should I do that you guide me?
Nay,
Your nslookup output suggests that your computer doesn’t have a DNS server configured. If you’re doing all of this in VBox, you’ll have to create an internal network for your virtual machine and the PFsense VM. This will allow the pfsense box to hand out DHCP information on the LAN interface to the virtual guest machine. At that point the guest will use the PFsense box for DNS. So your network would look like this:
INTERNET ———— EM0(WAN) on Pfsense+++++Internal routing on Pfsense++++++EM1(LAN) on Pfsense ———- Virtual Box Guest (guest and pfsense EM1 on internal virtual box network)
Thanks for the tutorial, However I have some questions regarding the configurations?
I’ve setup Pfsense on VM an cloud and I’ve assigned Public IP to WAN and Local IP like 192.168.3.1/24 to LAN and made this DHCP with a IP range like 192.168.3.10-192.168.3.254.
1. What rules or NAT should be configured in order the IP addresses received the IPs from DHCP to get out to internet?
2. How many Gateway is preferred to have and which one should be default?
3. In what situations should Static Route be configured?
Hope to hear you soon.
Thanks in advance,
Faruk,
1. The NAT rules would depend on your network and what needs to be translated. I can’t really provide any insight there without knowing more about the network.
2. Most of the time networks only need one gateway. You can configure multiple but the hosts will only be able to use one at a time.
3. Static route needs would again be dependent on your network setup. Most networks have a default static route out to the ISP and the ISP will generally have a static summary route back to the network. Regardless with PfSense in most home/small business situations, you won’t need to mess with static routes.
I have a three-router circuit. Both are linked to IPSEC to the main one. Everyone can see and enter. I’m running open to the main router. VPN client connections only see the main router’s network. I want to see all networks that connect to openvpn.
nice tutorial
thanks very much!
Ehsan,
You’re very welcome!