A firewall is a software that acts as a protective barrier between a user’s system and external networks, allowing or blocking packets based on predefined rules. Firewalls operate mainly at the network layer, handling both IPv4 and IPv6 packets.
The decision to allow or block a packet is based on rules defined in the firewall. These rules can be either built-in or user-defined. Each packet that enters or leaves the network must pass through this firewall, where it is evaluated based on these rules.
Linux systems provide multiple firewall management tools, with the most common being Firewalld and UFW. In this article, we will focus on these two tools, explaining their functionality and how to manage them on modern Linux distributions.
What is Firewalld?
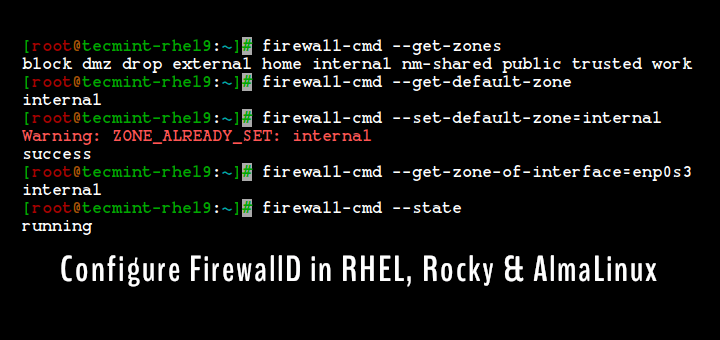
Firewalld is a dynamic firewall management tool that is included in many Linux distributions such as RHEL, CentOS, Fedora, and more. It provides a higher-level, user-friendly interface for managing firewall rules and network zones.
Firewalld allows two types of configuration:
- Permanent: These rules persist across system reboots.
- Runtime: These rules are temporary and are lost when the system or service restarts.
Firewalld organizes network traffic into zones, allowing different sets of rules for various networks, like public, internal, or trusted networks.
Firewalld’s configuration is stored in two directories:
- /usr/lib/firewalld: Default configurations that may be overwritten by system updates.
- /etc/firewalld: System-specific configurations that persist across reboots and updates.
Managing Firewalld Service in RHEL Systems
Here are some common commands to manage Firewalld on RHEL-based distributions:
Start Firewalld:
systemctl start firewalld
Stop Firewalld:
systemctl stop firewalld
Check Firewalld Status:
systemctl status firewalld
Check the state of Firewalld:
firewall-cmd --state
Enable Firewalld at boot:
systemctl enable firewalld
Disable Firewalld:
systemctl disable firewalld
Mask Firewalld (Prevents it from being started):
systemctl mask firewalld
Unmask Firewalld:
systemctl unmask firewalld
What is UFW?
UFW (Uncomplicated Firewall) is the default firewall management tool for Ubuntu and some other Linux distributions.
UFW is an easier-to-use frontend for managing firewall rules with iptables and it is designed to make managing a firewall simpler for users who do not need the full complexity of iptables.
Managing UFW Service in Debian Systems
Here are some common commands to manage UFW on Debian-based distributions:
Enable UFW:
sudo ufw enable
Disable UFW:
sudo ufw disable
Check UFW status:
sudo ufw status
Adding and Managing Rules with UFW
Here are the basic commands to manage UFW:
Allow a specific port on UFW (e.g., HTTP port 80):
sudo ufw allow 80
Deny a specific port on UFW:
sudo ufw deny 80
Allow SSH traffic on UFW:
sudo ufw allow ssh
Delete a rule on UFW:
sudo ufw delete allow 80
Enable logging for UFW:
sudo ufw logging on
Conclusion
In this article, we covered the basics of managing Firewalld and UFW in modern Linux distributions. Both Firewalld and UFW are powerful tools for managing network traffic and protecting your system from unauthorized access.
Firewalld provides dynamic firewall management with support for zones and complex rule sets, making it ideal for more advanced users and servers. UFW, on the other hand, is perfect for users who need a simpler and more user-friendly tool for managing firewall rules, especially on desktop or lightweight server environments like Ubuntu.
Understanding and using firewalls effectively is a crucial skill for anyone managing a Linux system, helping to secure your network from potential threats.




Is FIrewalld dependent on systemd?
@dragonmouth,
Yes, Firewalld is dependent on systemd. It uses systemd for managing its services. Firewalld runs as a daemon, and its service is started, stopped, and managed through systemd, typically via commands like:
I need to enable inbound/outbound traffic for ports any/any in Linux firewalls.
Can somebody please help me?
Thank you that was very helpful!!!
Hi, the first 2 commands are incorrect.
# systemctl firewalld start >> should be >> # systemctl start firewalld
# systemctl firewalld stop >> should be >> # systemctl stop firewalld
@Ryan,
Sorry its our bad, how come just silly mistake from our side, but thanks for correcting us…:)
No worries Ravi, I appreciate all the great content here.
Hello, great post.
Im starting to set some rules in my laptop, just a question, I have 2 NIC; eth0 and eth1. Both have internet connection, so i cant deny internet package from eth1? Thanks
@Kevin,
Yes, you can deny Internet traffic on particular NIC, in your case it is eth1 and the rule for iptables is: