GRand Unified Bootloader (GRUB) is a default bootloader in all Unix-like operating systems. As promised in our earlier article “How to reset a forgotten root password“, here we are going to review how to protect GRUB with a password.
As we mentioned before, someone can log in to single-user mode and change system settings, which is a big security risk. To stop unauthorized access, we need to protect Grub with a password in RHEL-based distributions such as Fedora, CentOS Stream, Rocky, and Alma Linux.
Here, we’ll learn how to stop users from getting into single-user mode and changing system settings, especially if they can directly access the system physically.
How to Password Protect GRUB Bootloader in Linux
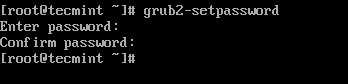
Create a password for GRUB, be a root user, and open the command prompt, type the below command.
grub2-setpassword
When prompted type grub password twice and press enter.
This will generate a hashed GRUB bootloader password in the file /boot/grub2/user.cfg file and can be viewed using the cat command as shown.
cat /boot/grub2/user.cfg
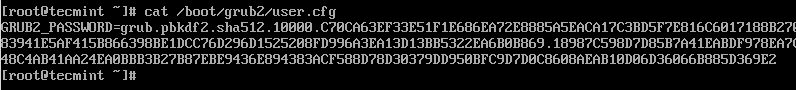
How to Generate New GRUB Configuration File
After creating the GRUB password, you need to re-create the new GRUB configuration file by running the following command.
grub2-mkconfig -o /boot/grub2/grub.cfg
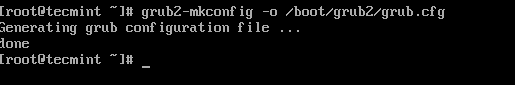
The above command will set the grub password in the configuration file. Now, reboot the system and check if the new GRUB password is set properly.
# reboot
How to Test GRUB Password Protection
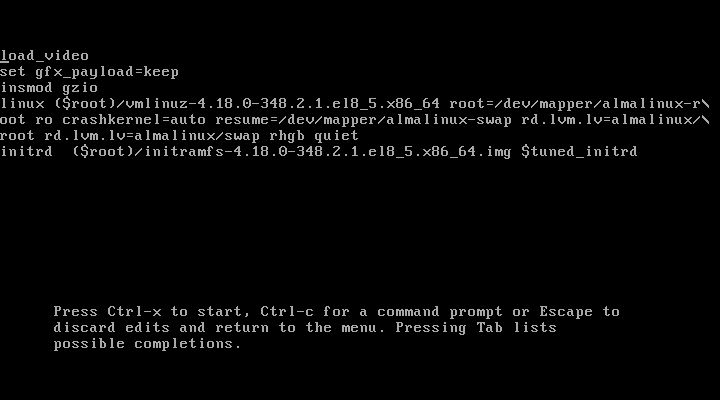
After your system restarts, you will get the following GRUB screen, where you will get 5 seconds to break the normal boot process. So quickly press e key to breaking the boot process.
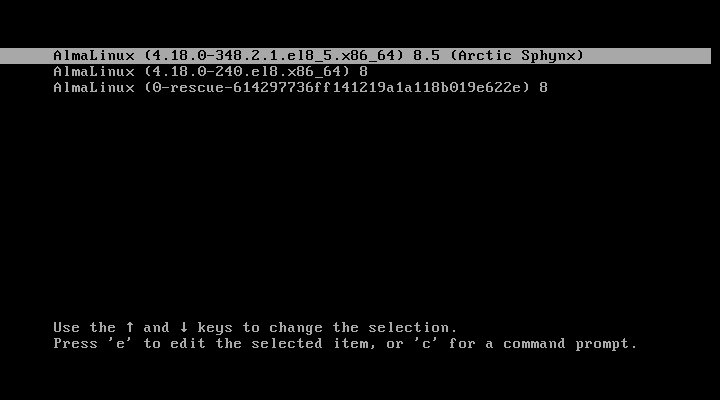
Once you press the e key it will prompt you to enter the GRUB password as shown.

After entering the right username and password, you can edit GRUB parameters as shown.
How to Remove GRUB Password Protection
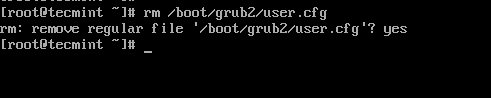
To remove GRUB password-protect from the boot menu, simply delete the file /boot/grub2/user.cfg.
rm /boot/grub2/user.cfg
This is how we can protect GRUB with passwords. Let us know how you secure your system? via comments.