In this brief tutorial, you will learn how to reset a forgotten root password in a Debian 10 system. This will help you regain the ability to log in as the root user and carry out administrative tasks.
So, first power on or reboot your Debian 10 system. You should be presented with a GRUB menu as shown below. On the first option, proceed and press the ‘e’ key on the keyboard before the system starts booting.
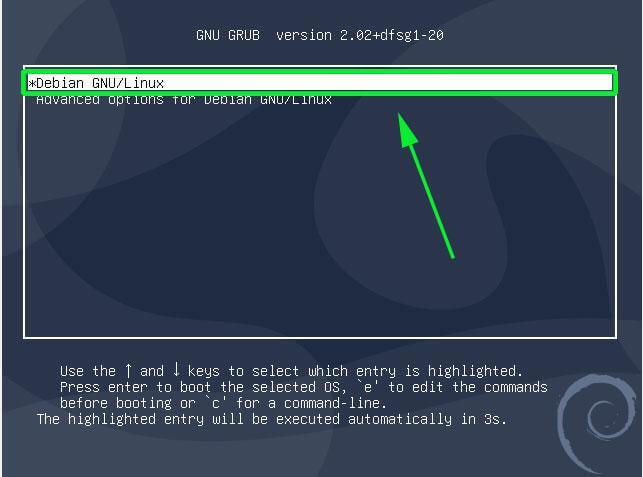
This ushers you to the screen shown below. Scroll down and locate the line that begins with ‘linux’ that precedes the /boot/vmlinuz-* section that also specifies the UUID.
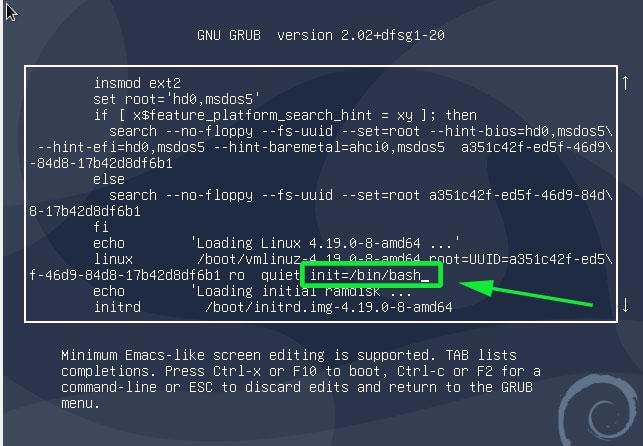
Move the cursor to the end of this line, just after ‘ro quiet’ and append the parameter init=/bin/bash.
Next hit ctrl + x to enable it to boot in single-user mode with the root filesystem mounted with read-only (ro) access rights.
For you to reset the password, you need to change the access right from read-only to read-write. Therefore, run the command below to remount the root filesystem with rw attributes.
:/# mount -n -o remount,rw /
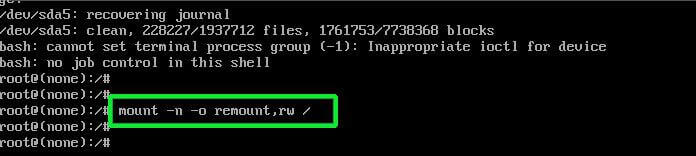
Next, reset the root password by executing the good old passwd command as shown.
:/# passwd
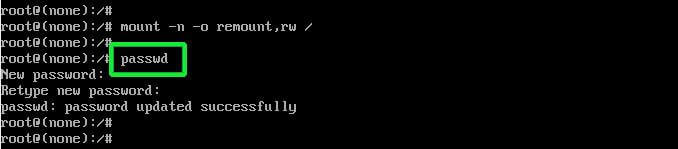
Provide the new password and retype it to confirm. If all went well and the passwords match you should get a ‘password updated successfully’ notification at the end of the console
Finally press Ctrl + Alt + Del to exit and reboot. You can now log in as the root user using the newly created password that you just defined.
And that’s how you reset a forgotten root password on Debian 10.






This worked. thanks James. Its a good post.
How to reset username and password in Debian please help?
Hello,
I have this error :
“Authentification token manipulation error”
and I can’t modify /etc/shadow permission
Have you an idea please?
Thanks
Hi Zafibiky,
Have you found a solution?
@Zafibiky,
The error could be caused by the filesystem being mounted as read-only. To resolve this, you may need to remount it with read-write permissions.
Following this, perform a filesystem check to ensure the integrity of the filesystem.
Once I reach the read-only line, I can not type in anything?
One year later, I hope you did find the answer in the mid-time. You simply have to select the second line where the mono/multi-user environment is set to single. It worked for me, I saw the message loading the keyboard drive and it did the trick.
Thanks James, I knew the way to do it but here the explanations are very simple to follow. Brilliant.
Hello!
I have not used my Debian 10 for almost a year. When trying to log back on, I keep getting the message that my password is incorrect, even after I followed all the steps in this article. I tried with different user names as well, but I know for sure that the first try was correct. What can I do in this case?
Thanks!
Hi,
When the GUI comes up, so far as I know, you cannot log in as root, you have to login as a user that you set up when you installed the system. So how does changing the root password help when it’s the user password you use to login and the one most people will need/have forgotten?
Hey Hugo, while you cannot log in as root via the GUI, changing the root password is helpful if you want to make system changes that require elevated privileges provided for by the root user. Imagine a situation where you want to changes to the system or add /remove new users but you have forgotten the root password.
Additionally, if you want to change a regular user’s password, you can do so in the very last step. Simply run
After I do all that, my installation boots to a prompt that says, “enter root password or press e to continue.”
So now anyone can access your system!
Hey David. Whilst the main purpose of this article is to show users how they can reset the root password, you can also configure your system to disable editing of the grub menu parameters. This effectively locks out anyone who would want to reset the root password.
Do people have physical access to your servers? Bad
Do people have access to your management/time? Bad
Can’t help the above? Use Luks Encryption
In IT, there’s been a saying for almost forever: ‘If I can touch your box, I own your box.’ Physical security is the last layer of security. If a stranger has access to someone’s box, you have a problem.
Almost every single piece of network and IT equipment has some form of physical reset, or the landfills would be full of perfectly functional equipment that just cannot be accessed