In case you are running Linux on a machine that you normally use alone, say on a laptop, entering a password each time you invoke sudo can become so boring in the long run. Therefore, in this guide, we will describe how to configure the sudo command to run without entering a password.
This setting is done in the /etc/sudoers file, which drives sudoers to use the default security policy plugin for the sudo command; under the user privilege specification section.
Important: In the sudeors file, the authenticate parameter which is turned on by default is used for authentication purposes. If it is set, users must authenticate themselves via a password (or other means of authentication) before they run commands with sudo.
However, this default value may be overridden using the NOPASSWD (require no password when the user invokes sudo command) tag.
The syntax to configure user privileges is as follows:
user_list host_list=effective_user_list tag_list command_list
Where:
user_list– list of users or a user alias that has already been set.host_list– list of hosts or a host alias on which users can run sudo.effective_user_list– list of users they must be running as or a run as alias.tag_list– list of tags such as NOPASSWD.command_list– list of commands or a command alias to be run by user(s) using sudo.
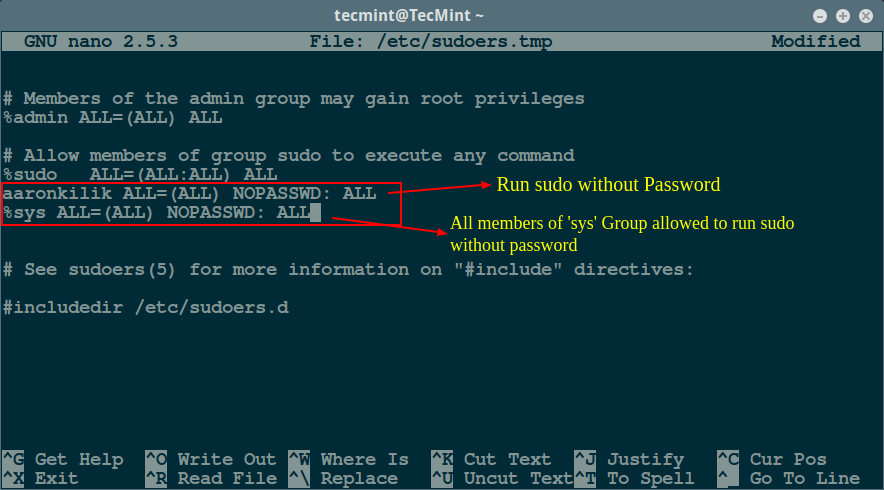
To allow a user (aaronkilik in the example below) to run all commands using sudo without a password, open the sudoers file:
$ sudo visudo
And add the following line:
aaronkilik ALL=(ALL) NOPASSWD: ALL
For the case of a group, use the % character before the group name as follows; this means that all members of the sys group will run all commands using sudo without a password.
%sys ALL=(ALL) NOPASSWD: ALL
To permit a user to run a given command (/bin/kill) using sudo without a password, add the following line:
aaronkilik ALL=(ALL) NOPASSWD: /bin/kill
The line below will enable members of the sys group to run the commands: /bin/kill, /bin/rm using sudo without a password:
%sys ALL=(ALL) NOPASSWD: /bin/kill, /bin/rm
For more sudo configuration and additional usage options, read our articles that describe more examples:
- 10 Useful Sudoers Configurations for Setting ‘sudo’ in Linux
- Let Sudo Insult You When You Enter Incorrect Password
- How to Keep ‘sudo’ Password Timeout Session Longer in Linux
In this article, we described how to configure the sudo command to run without entering a password. Do not forget to offer us your thoughts about this guide or other useful sudeors configurations for Linux system administrators in the comments.





Succinct and straightforward – my type of article!
In response to the question asked here: https://stackoverflow.com/questions/25189348/unable-to-provide-password-to-a-process-with-subprocess-python
On Linux you can bypass the sudo prompt using:
Pass the formatted command to subprocess and you are good to go:
````python import subprocess as sp cmd = "whoami" password= "" stdout, stderr = sp.Popen("echo {} | sudo -S {}".format(password, cmd), shell=True, stdout=sp.PIPE, stderr=sp.PIPE).communicate() print(stdout.decode()) if stderr: print("error occured:") print(stderr.decode()) ````It should print `root` as the command is executed by the sudo user.
Alternately you can use python pudo package: https://pypi.org/project/pudo/1.0.0/
Installation:
Below is the code snippet for using in python automation for running commands under root privilege::
user$ python3 # or python2 >>> import pudo >>> (ret, out) = pudo.run(('ls', '/root')) # or pudo.run('ls /root') >>> print(ret) >>> 0 >>> print(out) >>> b'Desktop\nDownloads\nPictures\nMusic\n'Below is the cmd example for running commands under root privilege
user$ pudo ls /root Desktop Downloads Pictures MusicHi,When I opened the sudo.conf, I find a default record, “root ALL=(ALL:ALL) ALL“, my question is what’s the meaning of the third ALL, Thanks.
@Hubo
The third ALL refers to effective groups, in this line, it means user root can run commands as all groups.
Follow my understanding, the syntax to add a record is ” =( [, …]:[ ,…]) “, is it right, Thanks.
Sorry, some mistakes have occured, the syntax to add a record , for example, “root ALL=(user1, user2: group1, group2) NOPASSWD: ALL”, is it right, Thanks.
@Hubo
Yap, according to the sudoers man page, which explains that, “Multiple users and groups may be present in a Runas_Spec(run as user or group), in which case the user may select any combination of users and groups.
In this example:
aaronkilik ALL = (root, bin : operator, system) ALL
The user aaronkilik may run any command as either user root or bin, optionally setting the group to operator or system. ”
For additional info, go through the sudoers man page:
man sudoers
I used
''around ‘username’, which was stripped out.That should be –
Defaults:username !authenticate
We will test this method as you have suggested, thanks for the feedback.
You can also add:
Defaults: !authenticate
Instead of configuring sudo to not require authentication at all you can setup pam_ssh_agent_auth to have it authenticate you by your ssh key.
@BasketCase
Many thanks for the useful suggestion. We will surely try this out.