Linux System is much secured than any of its counterpart. One of the way to implement security in Linux is the user management policy and user permission and normal users are not authorized to perform any system operations.
If a normal user needs to perform any system wide changes he needs to use either ‘su‘ or ‘sudo‘ command.
NOTE – This article is more applicable to Ubuntu based distributions, but also applicable to most of the popular Linux distributions.
‘su’ Vs ‘sudo’
‘su‘ forces you to share your root password to other users whereas ‘sudo‘ makes it possible to execute system commands without root password. ‘sudo‘ lets you use your own password to execute system commands i.e., delegates system responsibility without root password.
What is ‘sudo’?
‘sudo‘ is a root binary setuid, which executes root commands on behalf of authorized users and the users need to enter their own password to execute system command followed by ‘sudo‘.
Who can execute ‘sudo’?
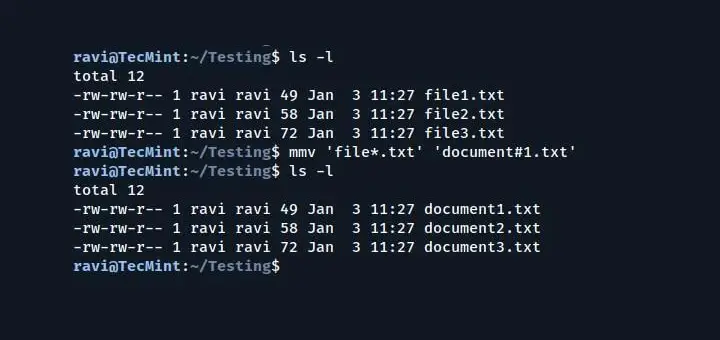
We can run ‘/usr/sbin/visudo‘ to add/remove the list of users who can execute ‘sudo‘.
$ sudo /usr/sbin/visudo
A screen shot of ‘/usr/sbin/visudo‘ file, looks something like this:

The sudo list looks like the below string, by default:
root ALL=(ALL) ALL
Note: You must be root to edit /usr/sbin/visudo file.
Granting sudo Access
In many situation, System Administrator, specially new to the field finds the string “root ALL=(ALL) ALL” as a template and grants unrestricted access to others which may be potentially very harmful.
Editing ‘/usr/sbin/visudo’ file to something like the below pattern may really be very dangerous, unless you believe all the listed users completely.
root ALL=(ALL) ALL adam ALL=(ALL) ALL tom ALL=(ALL) ALL mark ALL=(ALL) ALL
Parameters of sudo
A properly configured ‘sudo‘ is very flexible and number of commands that needs to be run may be precisely configured.
The Syntax of configured ‘sudo‘ line is:
User_name Machine_name=(Effective_user) command
The above Syntax can be divided into four parts:
- User_name: This is the name of ‘sudo‘ user.
- Machine_name: This is the host name, in which ‘sudo‘ command is valid. Useful when you have lots of host machines.
- (Effective_user): The ‘Effective user’ that are allowed to execute the commands. This column lets you allows users to execute System Commands.
- Command: command or a set of commands which user may run.
Suggested Read: 10 Useful Sudoers Configurations for Setting ‘sudo’ in Linux
Some of the Situations, and their corresponding ‘sudo‘ line:
Q1. You have a user mark which is a Database Administrator. You are supposed to provide him all the access on Database Server (beta.database_server.com) only, and not on any host.
For the above situation the ‘sudo‘ line can be written as:
mark beta.database_server.com=(ALL) ALL
Q2. You have a user ‘tom‘ which is supposed to execute system command as user other than root on the same Database Server, above Explained.
For the above situation the ‘sudo‘ line can be written as:
mark beta.database_server.com=(tom) ALL
Q3. You have a sudo user ‘cat‘ which is supposed to run command ‘dog‘ only.
To implement the above situation, we can write ‘sudo’ as:
mark beta.database_server.com=(cat) dog
Q4. What if the user needs to be granted several commands?
If the number of commands, user is supposed to run is under 10, we can place all the commands alongside, with white space in between them, as shown below:
mark beta.database_server.com=(cat) /usr/bin/command1 /usr/sbin/command2 /usr/sbin/command3 ...
If this list of command varies to the range, where it is literally not possible to type each command manually we need to use aliases. Aliases! Yeah the Linux utility where a long-lengthy command or a list of command can be referred as a small and easy keyword.
A few alias Examples, which can be used in place of entry in ‘sudo‘ configuration file.
User_Alias ADMINS=tom,jerry,adam user_Alias WEBMASTER=henry,mark
WEBMASTERS WEBSERVERS=(www) APACHE Cmnd_Alias PROC=/bin/kill,/bin/killall, /usr/bin/top
It is possible to specify a System Groups, in place of users, that belongs to that group just suffixing ‘%’ as below:
%apacheadmin WEBSERVERS=(www) APACHE
Q5. How about executing a ‘sudo‘ command without entering password?
We can execute a ‘sudo‘ command without entering password by using ‘NOPASSWD‘ flag.
adam ALL=(ALL) NOPASSWD: PROCS
Here the user ‘adam‘ can execute all the commands aliased under “PROCS”, without entering password.
Suggested Read: Let Sudo Insult You When You Enter Incorrect Password
“sudo” provides you a robust and safe environment with loads of flexibility as compared to ‘su‘. Moreover “sudo” configuration is easy. Some Linux distributions have “sudo” enabled by default while most of the distros of today needs you to enable it as a Security Measure.
To add an user (bob) to sudo just run the below command as root.
adduser bob sudo
That’s all for now. I’ll be here again with another Interesting article. Till then stay tuned and connected to Tecmint. Don’t forget to provide us with your valuable feedback in our comment section.