Step 3: Creating a XenServer Network VLAN
At this point the LACP bond is ready to be used. Since this particular LACP bond is a trunk, it will be important to create tagged external networks so that traffic will have the proper VLAN tag.
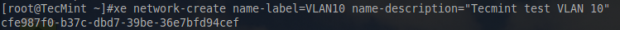
Let’s visit this process now. The first step is to create a new network for this particular VLAN. This is the same as what was done to create the bond in the first place.
# xe network-create name-label=VLAN10 name-description="Tecmint test VLAN 10"
As with all of the other xe commands, this one when successful, will output the UUID of the newly created network. Keep this handy as it will be needed soon.
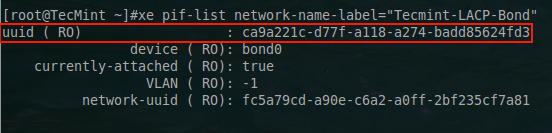
The next step is to determine the UUID of the PIF that this VLAN network will use. In this example, the LACP bond from the previous steps will be used to support VLANs. Using xe, the UUID of the bond interface can be determined.
# xe pif-list network-name-label="Tecmint-LACP-Bond"
This will return the UUID of the bond0 interface. This UUID will be necessary for the VLAN network so that the tagged traffic knows what interface to exit the XenServer.
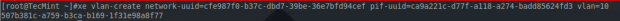
From this point all the necessary information is available to build the xe command to create a VLAN tagged network.
# xe vlan-create network-uuid=cfe987f0-b37c-dbd7-39be-36e7bfd94cef pif-uuid=ca9a221c-d77f-a118-a274-badd85624fd3 vlan=10
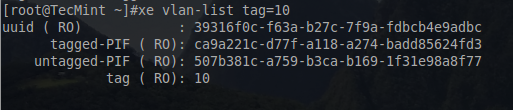
The UUID returned here indicates the host that this new VLAN network was created on and isn’t actually needed for any further steps. As with all steps, it is always a good idea to confirm that the changes were applied.
To confirm the new VLAN network:
# xe vlan-list tag=10
This will return the information for the VLAN 10 network just created as well as the associated PIFs.
This XenServer now has a LACP bonded network as well as one network that is ready to tag traffic for a VLAN 10. This VLAN 10 network can be added to a VIF (virtual interface) on a guest to allow guest traffic to be tagged by the virtual switch and sent across the trunk setup between the switch and the XenServer.




Thanks, Rob:
Can you recommend some way of identifying the UUID of the XenServer host’s Primary Management Interface (PMI) from the command-line?
TIA,
Eric Pretorious
Portland, Oregon
Eric,
Sure! xe pif-list management=true host-name-label= or if you want only the UUID only you can run the following command: xe pif-list management=true host-name-label= | head -1 | awk -F ‘: ‘ ‘{print $2}’
xe pif-list management=true host-name-label=
Output:
uuid ( RO) : 2ba82249-cc18-8525-3a3a-289890665e08
Device ( RO): eth0
currently-attached ( RO): true
VLAN ( RO): -1
network-uuid ( RO): 5798e0f4-d84a-ae3e-c090-709f70a016ac
xe pif-list management=true host-name-label= | head -1 | awk -F ‘: ‘ ‘{print $2}’
Output:
2ba82249-cc18-8525-3a3a-289890665e08
Thanks!
Nicely documented !!
Abhinav,
Thank you very much and hope it provided you will some useful information.